From an overall industry standpoint, 91% of security breaches begin with phishing or spear-phishing (Source: Wired), and Verizon’s 2017 Data Breach Investigations Report has said that one in 14 people clicked on a link or opened an attachment in a phishing message.
We’ve recently been told by many of our customers that they want to be better informed about prevalent phishing attacks so that they can proactively educate their team and protect against such attacks. Among various phishing attacks, here are the top four most common attacks that you’re most likely to see.
What can I do to protect my team against phishing attacks?
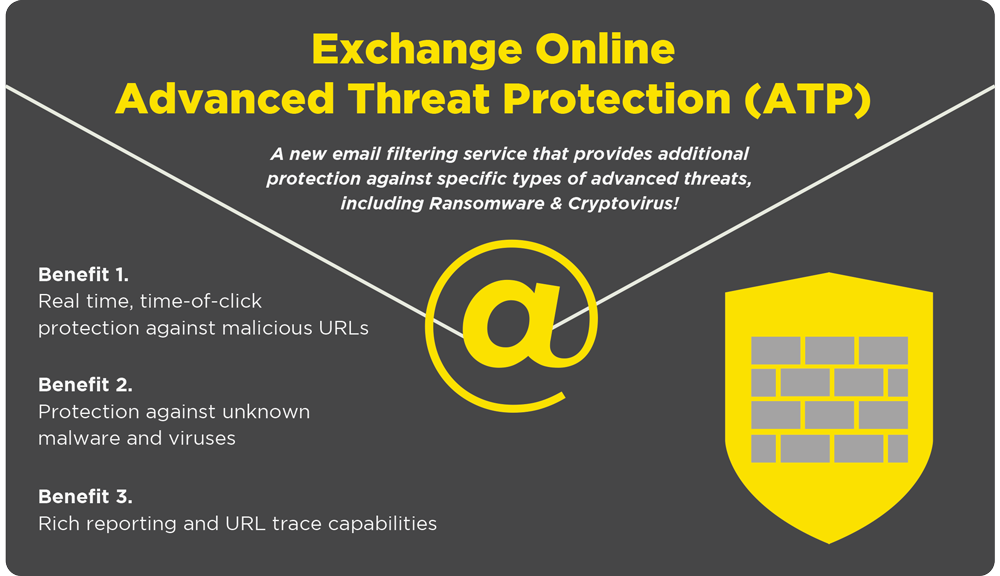
There are various tools you can implement to successfully detect phishing attacks. One inexpensive tool you can easily utilize is Microsoft Office 365 Advanced Threat Protection (ATP).
ATP helps protect your inbox from phishing attacks in various ways such as:
- Safe Attachments (protecting against unknown malware and viruses)
- Safe Links (protecting against malicious URLs at time-of-click)
- URL detonation (combination of Safe Attachments and Safe Links)
- Reporting and Tracing (providing URL trace and reporting on advanced threats)
- Office 365 ATP Enhanced Reporting (showing malware and spam trends in an organization)
Some of our team members have recently been targeted by attackers, but ATP flagged the phishing emails as fraudulent and alerted those who were targeted. Want to hear more about how we were targeted? We’ve put together a blog post about the phishing attacks we recently experienced:
Related: Phishing Scams: Our Own Experience, and Tips to Avoid Them
Protect Your Organization from Phishing Attacks
Whether you want to implement the ATP or want to discuss other ways to protect your organization from phishing attacks, our team is here to help. Drop us a line to get all your questions answered.
4 Common Types of Phishing Attacks
For those who would like to learn about the four common types of phishing attacks in greater detail:
1. Deceptive Phishing
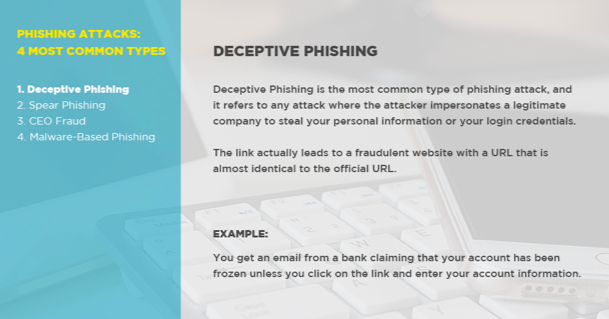
- What It Is: Deceptive Phishing is the most common type of phishing attack, and it refers to any attack where the attacker impersonates a legitimate company in an attempt to steal your personal information or your login credentials. The link actually leads to a fraudulent website with a URL that is almost identical to the official URL (typically only one letter will be out of place).
- An Example: You get an email from a bank claiming that your account has been frozen unless you click on the link provided and enter your account information.
2. Spear Phishing
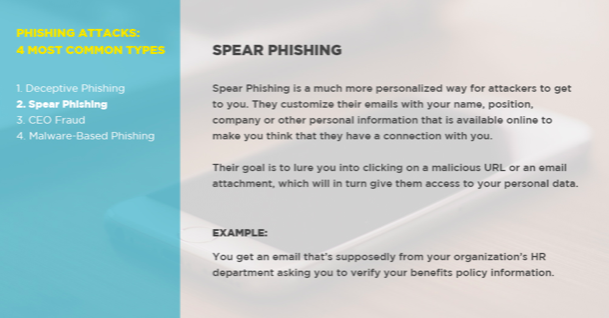
- What It Is: Spear Phishing is a much more personalized way for attackers to get to you. They customize their emails with your name, position, company, work phone number, or other personal information that is available online (typically through company websites or social media platforms like LinkedIn), in an effort to make you think that they have a connection with you. Their goal is to lure you into clicking on a malicious URL or an email attachment, which will in turn give them access to your personal data.
- According to this detailed Forbes article, the most effective spear phishing attacks are often the simplest and simply mimics the normal day-to-day operational activities that might occur in your own role within your organization.
- An Example: You get an email that’s supposedly from your organization’s HR department asking you to verify your benefits policy information.
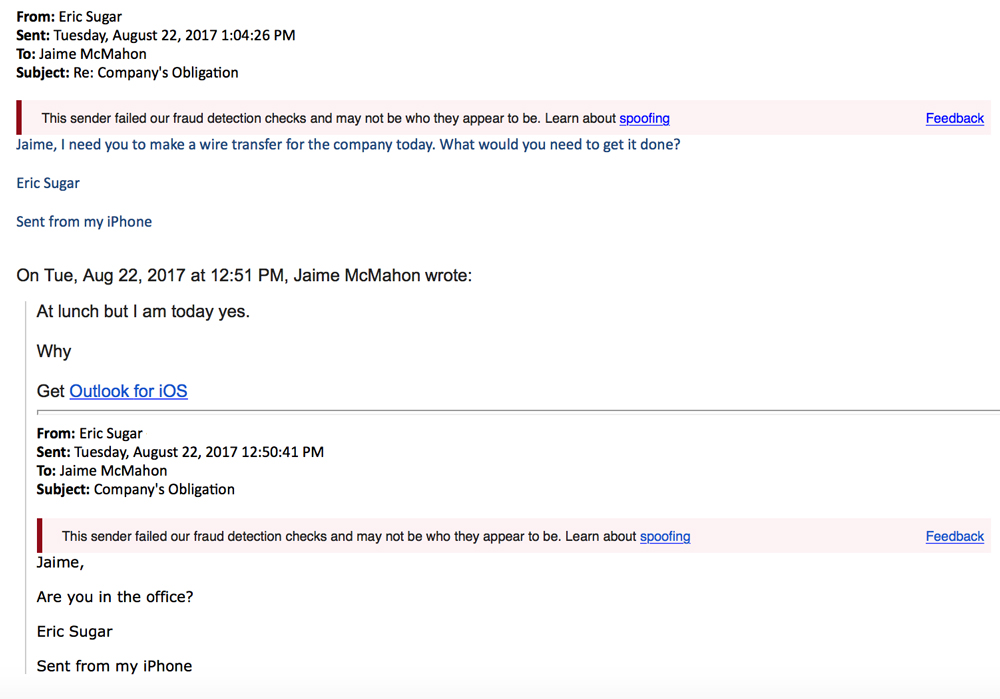
3. CEO Fraud
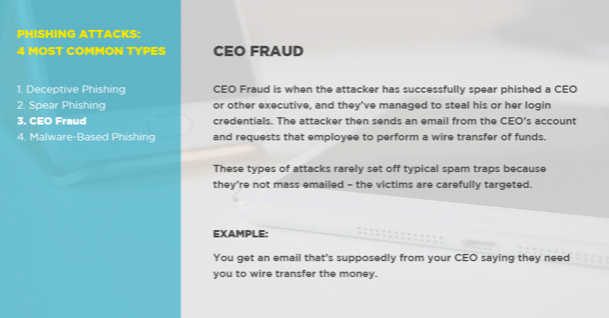
- What It Is: CEO Fraud is when the attacker has successfully spear phished a CEO or other top executive of the company (known as “whaling”), and they’ve managed to steal his or her login credentials. The attacker then sends an email from the CEO’s account, or creates a new domain name that’s off by one letter or number and duplicates the CEO’s credentials, and requests that employee to perform a wire transfer of funds to a financial institution of their choice.
- These types of attacks rarely set off typical spam traps because they’re not mass emailed – the victims are carefully targeted by the attacker.
- An Example: You get an email that’s supposedly from your CEO saying they need you to wire transfer the money, and to let you know when you’re free so they can send you the information of where it needs to go.
4. Malware-Based Phishing
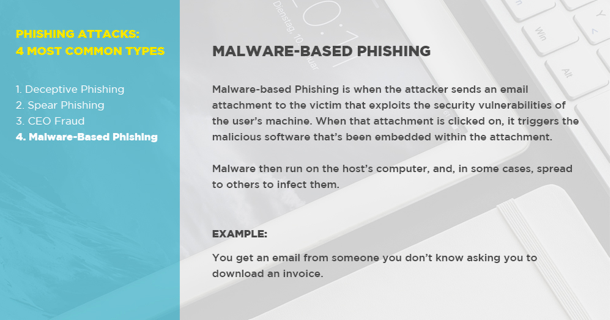
- What It Is: Malware-based Phishing is when the attacker sends an email attachment or downloadable file to the victim that exploits the security vulnerabilities of the user’s machine. When that attachment or file is clicked on, it triggers the malicious software that’s been embedded within the file/attachment.
- Malware (including computer viruses, worms, Trojan horses, ransomware, or other malicious programs) then run on the host’s computer, and, in some cases, spread to others to infect them (as in the recent “WannaCry” and “GoldenEye” ransomware attacks).
- An Example: You get an email from someone you don’t know asking you to download an invoice.
Get IT news & updates sent right to your inbox ✔️
Tags:
CybersecurityOctober 12, 2017



Comments