Every organization, regardless of size or industry vertical, is either under attack or already breached. 146 is the average number of days that an attacker has compromised a network before they’re detected. 65% of all network intrusions are due to stolen/compromised credentials.
The face of malicious activities is changing; from attempting to compromise systems via vulnerabilities to compromising the accounts used by employees. Cloud-based user account attacks have increased 300% between 2016 and 2017. Thus, the capability to have visibility into behaviours that may indicate such abnormal activities is paramount.
 |
Firewall is not designed to see this and in many cases, won’t prevent it. Common SIEM’s won’t detect legitimate actions being taken by end users and if they do, stringing the events together can be cumbersome. This is why Microsoft Advanced Threat Analytics, an advanced behavioural analytics tool, is the next evolution in any organization’s security posture. Advanced Threat Analytics intelligence provides increased visibility and reliability by reducing problematic false positives, which plague many of today’s solutions. |
By virtually eliminating the need for custom policy creation, Advanced Threat Analytics provides you with the clarity of information and suggested remediation options, included within the solutions alerts. The ability to transfer the initial triage of events to lower cost support personnel can now be realized. This allows for the specialized skillset of the SOC teams to focus on higher value initiatives by reducing their need to address “routine” investigations.
What is Microsoft Advanced Threat Analytics?
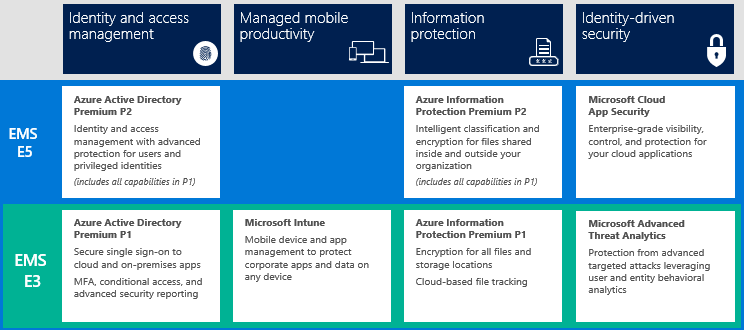
Advanced Threat Analytics (ATA) is one of many components within the Enterprise Mobility + Security solution offered by Microsoft.
Advanced Threat Analytics is a security incident reporting solution based on behavioral analytics, which means that the solution ingests large volumes of data to reveal statistical patterns of behaviour. Advanced Threat Analytics (an on premises solution) continually collects authentication data destined for Domain Controllers to determine a base line of what is normal for all identified entities on the network. Over time, as data is collected, Advanced Threat Analytics becomes more powerful by increasing its understanding of activities that are typical for the network in which it is deployed.
Advanced Threat Analytics also has the ability to read Active Directory and is able to contextualize an event prior to sending an alert. For example, if someone logs into a server that they have not logged into before, the event would be new and would raise a flag. Advanced Threat Analytics would then look at the group memberships of that individual to see if the action being performed is truly a risk. If the account aligns with the Active Directory permissions granted for the login and if the behaviour aligns with normal patterns for this user’s actions, then no alert would be raised within that context.
Now, if the same account had made multiple attempts to several servers that they did not have Active Directory permissions to access prior to the successful login, an alert would be raised for the failures but would also include the successful login as part of the chain of events. This second aspect also includes the ability for the Advanced Threat Analytics Centre to be updated via signatures that allow for the alerting of any readily identifiable security concerns such as “pass the hash” attacks.
Advanced Threat Analytics (ATA) Deployment Components
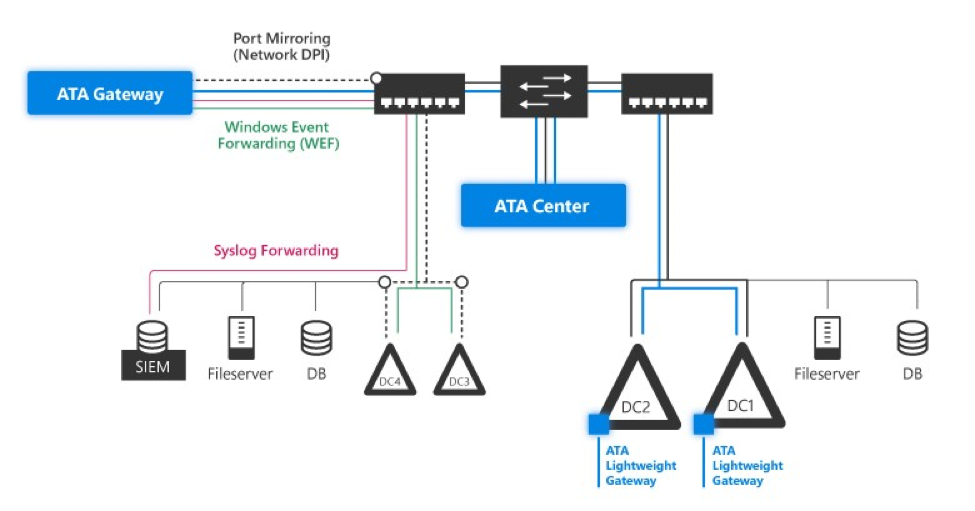
ATA Centre is the server that acts as the brains behind the monitoring solution. The ATA Centre houses the solutions configuration and provides the alerting services.
ATA Gateway is configured as part of an egress span port on a network switch in which a Domain Controller is a member of. An ATA Gateway should be deployed on every switch in which a Domain Controller is present and is the preferred topology. The gateway is promiscuous, capturing all Active Directory events destined the Domain Controller(s) located on the same switch. Data gathered is then forwarded to the ATA Centre for processing.
ATA Lightweight Gateway is an agent-based alternative to the ATA Gateway. The lightweight gateway would be deployed on every Domain Controller in which there is no gateway located on the same switching span port as the Domain Controller. This solution would be suitable for remote locations such as branch offices.
Note:
- Lightweight gateways do not have the same throughput as their server counterparts.
- Windows events, Syslog and SIEM events can be sent to either gateway for ingestion into the ATA Centre for analysis.
Advanced Threat Analytics requires a minimum of Windows 2012R2 for deployment.
Advanced Threat Analytics Reporting - 2 Major Benefits
Advanced Threat Analytics Reporting Benefit 1: It’s Efficient
As described earlier, Advanced Threat Analytics builds its alerts and actions on patterns based on historical data through a combination of information stored within its database, reading Active Directory for the entities’ permissions, as well as known attack signatures such as “pass the hash” attacks. Based on this information, Advanced Threat Analytics then makes a calculated decision as to the likelihood of the event being a legitimate breach of security or a permitted operation.
With this methodology, security operations centres see less “noise” compared to more traditional rules-based solutions. The affect is that SOC teams don’t become overburdened with false positives, allowing the team to focus on credible incidents.
Advanced Threat Analytics Reporting Benefit 2: It’s Comprehensive
Advanced Threat Analytics alerts are designed to be clear and decisive. The report is divided into the following three sections:
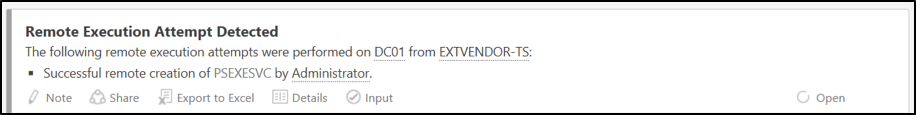
- A description of the event that occurred which triggered the alert, including who and what was involved in the incident.
- Indication of the event’s success or failure.
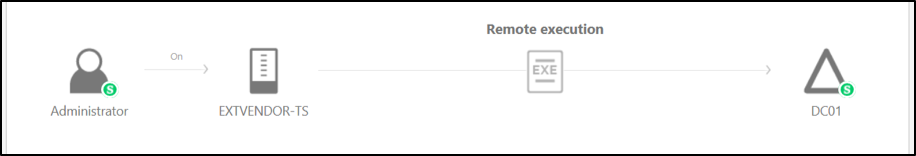
- An easy to understand graphical representation of all entities evolved in the alert.
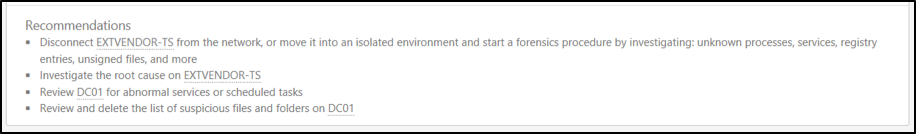
- A list of immediate actions to take intended to remediate the risk(s) identified by Advanced Threat Analytics.
Next Steps - How to Get Started with Advanced Threat Analytics
Until September 29, 2017, ProServeIT is offering a no cost gateway requirements analysis to help your organization plan for the deployment of Advanced Threat Analytics. This includes:
- Conducting a sizing exercise via tools specifically designed to identify the appropriate gateway requirements for your infrastructure.
- The creation of a proper gateway topology given Domain Controller traffic on your network.
- Conversations surrounding the use of lightweight gateways vs the use of port mirroring
- Topology diagram for all the above including the Advanced Threat Analytics server sizing requirements.

If you are interested in learning more about Advanced Threat Analytics, we encourage you to watch our on-demand webinar that we co-presented with the Microsoft security team. It includes a live demo of Advanced Threat Analytics.
Tags:
CybersecuritySeptember 07, 2017



Comments