As the leaves change colors and the air turns crisp, October not only marks the arrival of fall but also a crucial annual observance: Cybersecurity Awareness Month. This month-long campaign continues its mission of educating and empowering individuals and organizations to stay vigilant in the ever-evolving world of digital threats.
In this blog post, we delve into the heart of cybersecurity with a spotlight on critical topics and insights to safeguard your digital realm. We will also briefly explore the MGM Resorts ransomware attack which occurred last month, take a visionary glimpse into Microsoft's Security Copilot, and explore how nudges and AI are revolutionizing defense against cyber threats.
So, fasten your digital seatbelts and prepare for an enlightening journey through Cybersecurity Awareness Month, as we navigate the treacherous waters of today's online world and equip ourselves with knowledge, tools, and strategies to protect our digital assets and privacy.
In a hurry? Jump straight to your section of interest:
🔒 Safeguarding Your Company’s Digital Environment⚙️ Ransomware Attack Review: Lessons from MGM Resorts
🤖 Unlocking the Power of AI in Cybersecurity with Microsoft Security Copilot
🧠 How Nudges and AI can Help Your Organization’s Cybersecurity
🏁 Conclusion
Cybersecurity Awareness Month: Safeguarding Your Company's Digital Realm
In today's digital age, where cyber threats lurk around every virtual corner, cybersecurity awareness is not merely a suggestion; it's a necessity. As we celebrate Cybersecurity Awareness Month, it's crucial to recognize the evolving landscape of digital risks and take proactive steps to protect our data and internet-connected devices.

Image: Key statistic from Microsoft’s 2022 Digital Defense Report
According to data from the 2022 Microsoft Digital Defense report, 80% of security incidents can be traced to missing elements that could be addressed through modern security approaches.
One alarming statistic underscores the urgency: the median time for an attacker to access your private data through a phishing email is 1 hour and 12 minutes.
To fortify our digital fortresses, we must prioritize device management by doing the following:
1. Keep your devices secure by regularly updating their software with the latest security patches. Consider enabling automatic updates to streamline the process and minimize vulnerability to ransomware and malware.
2. Meticulously review and adjust privacy and security settings, tailoring them to your desired level of information-sharing whenever you create new accounts, download apps, or acquire new devices.
3. Implement attack surface reduction rules to block known threats associated with specific software behaviors, such as suspicious script executions or abnormal app behaviors
To further bolster your defenses, pay special attention to internet-exposed endpoints, which are often favored entry points for attackers seeking access to an organization's assets. Regularly maintain your software, ensuring it remains updated and supported, and take the necessary steps to isolate, disable, or retire insecure systems and protocols. Additionally, fortify your digital perimeter by employing host-based firewalls and network defenses to block unexpected traffic.
Embracing these practices will empower you to defend your digital realm effectively.
12 Essential Tips for Safeguarding Your Data and Internet-connected Devices
Want to take your cybersecurity to the next level? Download a PDF infographic with 12 essential tips. Stay vigilant, stay secure, and protect what matters most.
Lessons to Learn from MGM Resorts' Cybersecurity Breach (September 2023)
The cybersecurity breach at MGM Resorts last month serves as a stark reminder of the substantial risks and consequences associated with ransomware attacks and data breaches. Here's a breakdown of the key takeaways:
1. Costly Consequences: MGM Resorts incurred a staggering $100 million in losses due to the ransomware attack. This eye-watering figure not only represents the direct financial impact but also highlights the potential long-term costs associated with such incidents.2. Extensive Impact: The cyberattack disrupted a wide array of MGM's business operations, affecting not just its main website but also online reservation systems, in-casino services, and more. This underscores the far-reaching consequences that can result from a single breach.
3. The Role of Social Engineering: The breach was executed by an affiliate of a known ransomware gang using social engineering tactics. This underscores the importance of employee training and vigilance in identifying and thwarting social engineering attempts.
4. Data Encryption: The hackers encrypted over a hundred ESXi hypervisors, effectively locking MGM out of its own systems. Implementing robust encryption practices and ensuring secure backup solutions is essential for preventing data loss in such situations.
5. Immediate Response: MGM Resorts incurred additional costs of under $10 million for risk remediation, legal fees, third-party advisory services, and incident response measures. This highlights the importance of having a well-prepared incident response plan to mitigate the impact of an attack.
6. Cybersecurity Insurance: MGM's ability to recover its losses through cybersecurity insurance is a testament to the importance of having a comprehensive insurance policy in place to cover potential financial losses.
7. Data Protection: The breach exposed some Personally Identifiable Information (PII) of customers who had transacted with MGM before March 2019. Protecting customer data should be a top priority, emphasizing the need for stringent data security measures and regular security audits.
8. Transparency and Communication: MGM Resorts acted transparently by disclosing the breach and providing updates on the incident. Effective communication and transparency are crucial for maintaining customer trust during and after a breach.
9. Ongoing Vigilance: MGM believes the incident has been contained, but ongoing vigilance and monitoring of systems are essential to prevent future breaches. Cybersecurity should be an ongoing commitment, not just a one-time effort.
In conclusion, the MGM Resorts cybersecurity breach serves as a poignant reminder that cybersecurity is not an option but a necessity for businesses. To safeguard against ransomware attacks and breaches, it's crucial to invest in robust cybersecurity measures, employee training, and an effective incident response plan to minimize the impact of such incidents and protect customer data.
Don’t wait for your organization to have a ransomware story! Proactively defend against cybersecurity threats with help from an AI-powered security system.
Unlocking the Power of AI in Cybersecurity with Microsoft Security Copilot
In the ever-evolving world of cybersecurity, defenders have long grappled with the daunting task of combating relentless and sophisticated attackers. The odds have remained stacked against them, exacerbated by the global shortage of skilled security professionals, leaving millions of job openings unfilled. However, Microsoft is ushering in a new era of security with its groundbreaking product, Microsoft Security Copilot, which harnesses the power of AI to tip the scales in favor of defenders. This product is currently in preview and not yet generally available.
Microsoft Security Copilot represents a paradigm shift by combining the company's leading security technologies with the latest advancements in AI. It operates at machine speed and scale, empowering security professionals to respond swiftly to threats that were once concealed amidst the noise.
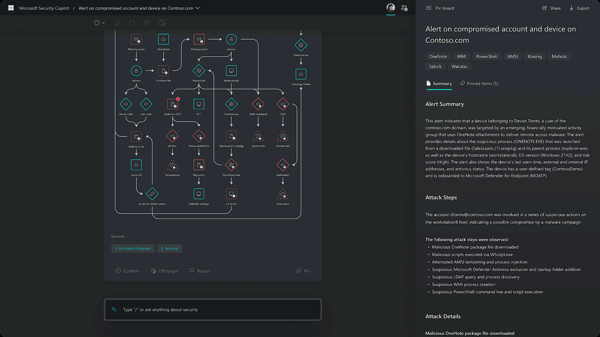
Image: Visual of Microsoft Security Copilot reporting on a cybersecurity incident
The product's unique combination of large language models and security-specific skills, informed by Microsoft's global threat intelligence, enhances the quality of detection, response speed, and overall security posture. Furthermore, Security Copilot is designed as a closed-loop learning system, continually improving its responses based on user interactions and feedback.
One of the key principles guiding Microsoft Security Copilot is its commitment to privacy and data protection. Your data remains under your control, never used to train AI models beyond your organization, and is safeguarded by robust security controls. Security Copilot is a collaborative tool, enabling security teams to work together effectively, accelerate incident response, and collectively develop their skills.
With this innovative approach, Microsoft will greatly assist businesses with the following cybersecurity concerns:
- Bridging the talent gap to enhance overall security capabilities
- Security Copilot enhances security teams' effectiveness by providing adaptive support, learning from interactions, and enabling them to achieve more with fewer resources.
- Simplifying complex security tasks
- Security Copilot empowers defenders to respond to security incidents within minutes by providing step-by-step guidance and customizable reporting, streamlining incident investigation and response.
- Helping your security team catch what others miss
- Security Copilot enables defenders to detect and prioritize threats, leveraging Microsoft's global threat intelligence and expert skills to uncover and anticipate malicious behavior in real-time.
In a world where every minute counts, Security Copilot delivers step-by-step guidance, real-time threat prioritization, and expert-level support, enabling security teams to operate with the agility and capabilities of a larger, more mature organization. By prioritizing responsible AI practices, Microsoft is not just transforming cybersecurity; it's setting a new standard for secure and ethical AI solutions.
Want to learn more about Microsoft Security Copilot? Click the video play button below to watch a short demo.
Empowering Cybersecurity with AI and Nudging: Defending Organizations on All Fronts
The world of cybersecurity is a battlefield where organizations constantly fend off relentless threats from cybercriminals. Ransomware attacks, in particular, have the potential to compromise data, disrupt operations, and demand hefty ransoms. To fortify their defenses, organizations are adopting a comprehensive cybersecurity strategy that aims to thwart attackers at the pre-ransomware stage. In this digital arms race, the concept of nudging, as defined by Cass Sunstein and Richard Thaler, finds a surprising ally in artificial intelligence (AI).
Nudging, fundamentally, is a gentle push in the right direction, guiding individuals towards choices that are in their best interest. This concept can be aptly applied in the realm of cybersecurity. AI, with its ability to maintain freedom of choice while steering users towards secure decisions, aligns perfectly with the principles of nudging. One example of this alignment is the use of AI-powered warnings and reminders to encourage users to update their software and protect their devices. This not only helps individuals make more informed decisions but also contributes to an organization's overall security posture.
 The evolution of nudging has seen an increased emphasis on protecting not only individual users but also third parties and broader social goals. For instance, organizations are using AI to nudge employees towards security best practices, such as enabling automatic updates and adopting robust privacy settings. This approach serves the dual purpose of safeguarding the organization's digital assets while promoting a culture of security awareness. It's a prime example of how nudging, combined with AI, can benefit both individual choice makers and the larger community.
The evolution of nudging has seen an increased emphasis on protecting not only individual users but also third parties and broader social goals. For instance, organizations are using AI to nudge employees towards security best practices, such as enabling automatic updates and adopting robust privacy settings. This approach serves the dual purpose of safeguarding the organization's digital assets while promoting a culture of security awareness. It's a prime example of how nudging, combined with AI, can benefit both individual choice makers and the larger community.
To tackle the labyrinthine world of cybersecurity effectively, organizations must address not only external threats but also the complexities within. AI, in collaboration with nudging principles, can aid in designing choice architectures that steer users towards safer options. For example, AI can nudge users towards opting for security features by default, enhancing their privacy and minimizing exposure to threats. As organizations prioritize cybersecurity awareness, nudging, and AI-driven practices, they set the stage for robust defenses that protect against the evolving landscape of cyber threats.

Conclusion
In closing, with Cybersecurity Awareness Month 2023, we aim to enlighten and empower you through discussions on safeguarding your digital environment, learning from the MGM Resorts ransomware attack, exploring the power of AI in cybersecurity, and identifying the role of nudges and AI in enhancing your organization's security.
The digital landscape is ever-changing, making vigilance and preparedness imperative. Take the next step by exploring Microsoft Funded Security Workshops to protect your digital assets effectively.
Cybersecurity is an ongoing commitment, so keep adapting, learning, and strengthening your defenses. Thank you for joining us on this journey; we're here to navigate the ever-evolving realm of digital security with you. Stay safe, stay vigilant, and keep your digital fortress secure!
Stay up to date with ProServeIT! 📨
Our monthly newsletter has all that as well as insightful information on relevant technology, webinars and workshops. Make sure to sign up now for your dose of tech knowledge delivered straight to your inbox!
Tags:
Tech News
October 20, 2023


Comments