Data security and protection is a crucial aspect for any organization today. With various data security measures implemented in place, there are still some challenges that IT decision-makers are concerned about when it comes to protecting their digital data.
This blog examines the current challenges with data security and how you can protect your data in the cloud.
Challenges organizations face with Data Security:
Protecting information in a mobile world
According to statistics, 2.5 quintillion bytes of data is created every day by web users and sensitive corporate data is created by your employees on a daily basis. With a large amount of data being created and stored, the first thing to do is to identify which information you absolutely need to put the proper protection in place.
Related Blogs
Protect Your Digital Assets with a Managed Cybersecurity Solution
What is Social Engineering & 4 Ways to Prevent Attacks
Storing sensitive data in the cloud
Cloud adoption has sharply increased especially recently due to the pandemic. According to a report, 83% of organizations have their most confidential data unencrypted in the cloud. And there is an average of around six months between infiltration of your data and detection. So, it might be difficult to even know that someone has stolen data until it's too late. Having the right security measure to protect the information stored in the cloud is important.
📧Sending sensitive information to the wrong person
According to research, about 58% of users have accidentally sent sensitive information to the wrong person. Imagine if you send sensitive company or client information to the wrong person. This could result in data breach affecting both company reputation and loss of customer trust.
💾 Not Having Secure Data Backups
Organizations need to understand the importance of having data backups and not just backups but having secure and encrypted backups.
Data Backup along with a disaster recovery plan is important as it ensures that your business can come back online in a timely fashion. Disaster recovery plan that meets your business requirements can help you minimize recovery time, potential delays and add to your overall security measures.
How can you protect your cloud data?
It is critical for companies to understand the importance of data security and protection as it can have heavy repercussions – both financially and reputationally. Organizations need to be focusing on both Data security (protecting data against unauthorized access or use) and Data Protection (creating backups of data in case of accidental data loss). There are different ways to mitigate security threats or risks.
Data loss prevention (DLP)
Data loss prevention (DLP) consists of tools and processes that protect sensitive data from getting lost, exploited, or accessed by unauthorized users. This software classifies regulated, confidential and business critical data and identifies violations of policies defined by the organization and their compliance team.
With DLP, we can control how sensitive data is shared via email, SharePoint, One Drive, Teams, etc. The DLP engine blocks sensitive emails and documents from going out of the organization and prevents the intentional or accidental exposure of sensitive information to unwanted parties. You can think of this as drawing a fence around your sensitive data stored in the Microsoft 365 cloud.
Your compliance team can either approve or decline the request depending on the content. You can also apply automatic encryption and still allow the user to send sensitive information (but at least with encryption). You can control how you want these DLP policies to be put in place and what level of protection you want to apply against it.
Protect sensitive information by encrypting emails
Any sensitive information relayed via email can be protected from being printed, forwarded or copied by unauthorized people, by configuring transport rules in Office 365. It automatically encrypts emails based on the content of the email or based on certain keywords. Or a user can manually encrypt the email directly from their Outlook client account.
When an Office 365 user sends an email, it would be scanned by the transport rule for any confidential content (be it the subject line or the email itself or even the attachment). Any type of personal information or information related to your business will be encrypted.
Once the email meets that transport rule, it gets encrypted, or the user can just click on the Encrypt button from their Outlook client and it would be encrypted throughout the email transfer conversation. The encrypted email remains in cipher-text while it is in transit to protect it from being compromised.
Conditional Access App Control
Another way we can control how data is protected is with conditional access app control. Conditional Access App Control gives us the ability to control the device we use to download, access and upload data within our environment. For example, if a user is trying to use their personal device and they try to download sensitive information, it would be blocked. They will not be able to download it.
Another example of conditional access app control is when a user signs into SharePoint, they have to abide by whatever conditional access policies are in place. That’s the first step. If a policy states that sign in is allowed only from Canada then any attempt to sign in happening outside of Canada will be rejected by the conditional access policy.
Microsoft information protection or MIP
Microsoft information protection (MIP) can identify, label, protect, monitor, and revoke access to documents in our environment. The first step here is to figure out what kind of sensitive information you want to protect. It could be any confidential data related to your business. Labels for such data can be created and tagged as general, personal, HR, Health, etc. These labels are further applied to the required documents and can be accessed by only authorized users.
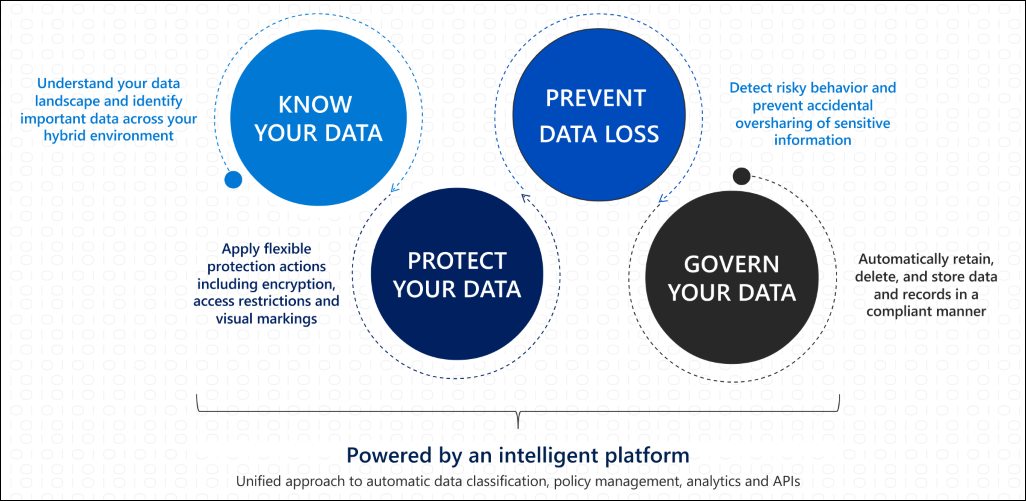
MIP or information protection in conjunction with DLP policies can prevent data loss (accidental or intentional) from your environment and the users receiving the encrypted documents will be able to open them if authorized. The encryption blocks everyone outside of the authorized users from opening the documents. And finally, you should govern your data with retention policies to retain, store and delete data according to your organization's requirements.
How To Protect Your Data?
Join ProServeIT for our third webinar in our Cybersecurity Framework series, as we look at how you can protect your corporate data and information, and preventing your users from inadvertently or inappropriately sharing it. Sign Up Now
Ready to Protect Your Data?
If you’re looking for ways to increase your security posture and protect your data in a cost-effective and efficient way, then ProServeIT’s Alarm Guardian could be the exact managed security solution you’re looking for.
ProServeIT’s Alarm Guardian:
☑️ Includes the installation of your new digital “security system”, so that you can protect your digital assets.
☑️ Proactively monitors alerts that are coming from your environment and helps to distinguish between false positives and legitimate threats.
☑️ Identifies new places where protections are required and takes proactive action to ensure any cybersecurity gaps are filled.
☑️ Provides contextual insights that further ensure all your digital assets are secure.
Our Alarm Guardian offer page provides further information on the three tiers of protection available for your organization, and be sure to book a call to discuss your organization’s unique requirements.
Content from: Cybersecurity Framework Webinar Series by George Abou-Samra
Edited by: Nikita Gill and Betty Quon
Tags:
AzureOctober 13, 2021




Comments