It wasn’t that long ago that email didn’t exist. Now, in just over 20 years, it’s become the second most important business communications tool after websites. Unfortunately, it’s also become one of easiest ways for your network and your data to be compromised. And the hackers are always ahead of the defenders. Research has shown that 70-75% of all incoming email is illegitimate.
Don't assume you are immune if you are a small business
Everyone is vulnerable, including small businesses. Email attacks are mostly meant to:
- Disrupt email communications
- Harvest business user information (name, address, password, credit card)
- Change data to disrupt user operations and compromise their identity
- Trick users into giving up their personal or corporate data (by indirect or social engineered attack)
As you can see, any target, large or small, can be vulnerable to these attacks. You can’t afford to take email security lightly. You have to watch it like a hawk.
Who are the attackers?
Email attacking is a serious business with some serious actors:
- National Governments (directly or through allied agents working on the government’s behalf)
- Criminals and criminal groups (both highly organized or ad hoc)
- Hacktivist groups who are trying to make political statements
- Bot attackers – automated applets that infiltrate systems and can cause much damage or steal information
- Insiders – disgruntled employees who may be able to compromise your system for nefarious reasons
- Amateurs who look for peer prestige engaging in malicious activity
Where do hackers obtain email addresses to attack?
The answer to this is just about any electronic source of communication. In 2017, it’s almost impossible for a business to function without electronic transactions. Many of these already have email addresses as part of the transaction. Even if they don’t, hackers have devised means to obtain them indirectly. All of these are referred to as Phishing Attacks; a play on words as the hackers are “fishing” for someone to bite on a malicious email “hook”.
Some important sources for Phishing include:
- Social web and messaging sites (possibly the number one place for email attackers to look for victims)
- Auctions sites (eBay and similar websites)
- Banking (by sending out false emails on realistic headers asking for banking or credit information)
What are the attackers looking for?
National Governments
- Cyber espionage, sabotage, and general cyber warfare are common among nation states as a natural evolution of covert warfare and intelligence gathering.
Criminals and Criminal Groups
- Generally driven by financial gain. Online fraud and identity theft are carried out using a multitude of spam, phishing, and malware attacks.
Hacktivist Groups
- Activism in a digital setting. For example, “Anonymous” is a highly capable group of hackers who target and compromise government and industry computers. Information stolen from agencies include identities of employees, executives, and business relationship details between companies and government agencies.
Bot Attackers
- Hackers, but with a different purpose. They want to compromise a system and take control to carry out other hacking activities like phishing schemes, spam, or malware attacks. Once control is gained, they can sell this control on the black market.
Insiders
- A disgruntled member of an organization is a constant problem nowadays. They may not have expertise in hacking, but they will have organizational system understanding, often allowing access to valuable data.
Amateurs
- Amateurs break into networks for self-fulfillment, bragging rights or some financial gain. They often download attack scripts and protocols already created by other hackers. They use sophisticated tools but with simple execution.
3 types of malicious emails you can expect
Unwanted advertisements
- These may considered the electronic equivalent of junk mail or they could be Trojan horses for more damaging attacks.
Financial matters
- These are often fraudulent attempts at getting a user to send out personal or corporate financial data. The malicious email tricks the user into doing this by looking so much like a real email, the user can’t often tell the difference.
Adult related
- As with unwanted advertisements, these emails may be trying to direct users to an adult related website (junk) or to use the adult site as a front for installing non-email delivered hacking software.
Of course, there are other kinds of malicious emails that you must watch out for. The above three are the most common kinds of attacks.
The damage email attacks can do
- Email spam has the potential to be the largest productivity decreasing and economic drain known today. If there were no anti-spam technologies, economic losses are estimated in the trillions.
- The USA spends between $20-$50 billion annually in costs due to spam and email protection.
- For spam to be profitable, it is estimated that only 1 in 25,000 spam recipients need to make a gray-market purchase.
Email Attacks are Constantly Evolving
- The only constant in security is change. The fact that you are secure one day may not mean anything the next day. The fact of the matter is, that you are under attack. You may not know it, but your systems, network, data, and users are all under threat and risk to be compromised with some malicious intention.
- The rise of more targeted attacks have significantly increased the size of the threat landscape.
Let us help you with your organization’s email security!
Having an email security plan and a defence in place will make your business safer. Now is the time to strengthen your organization’s email security by implementing an effective email security plan to watch your email like a hawk. Remember: now it’s not a matter of if you have a security incident, but when.
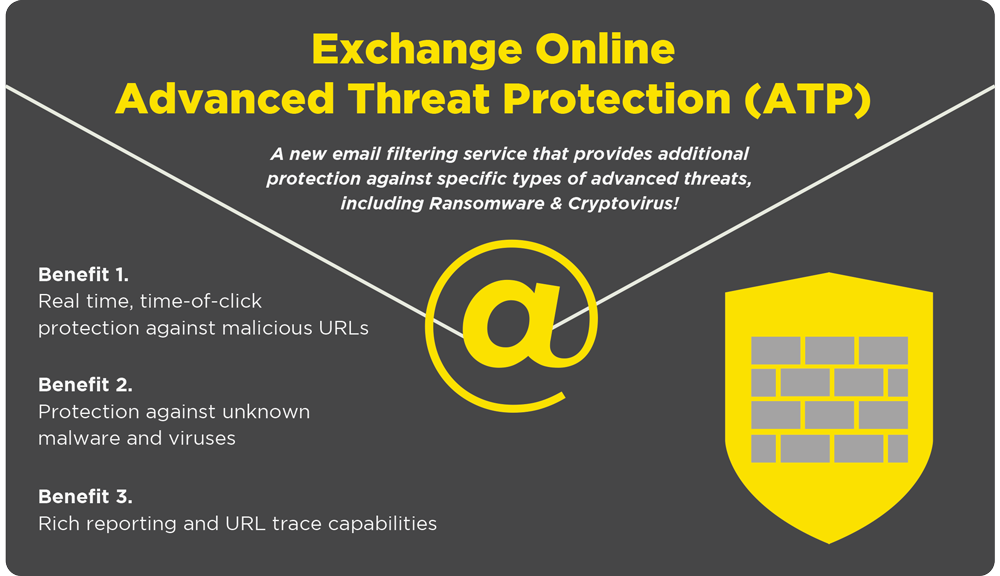
Exchange Online Advanved Threat Protection is the first tool that we recommend to our customers as this is very easy to install and inexpensive way to improve your email security. Questions? Drop us a line anytime!
February 23, 2017



Comments