It’s no secret that the Novel Coronavirus has made headlines globally over the past few weeks. However, this tragic illness that is striking so many people down is far more important than the health implications that come along with it!

That’s because Threat Actors (hackers, to some) are using Novel Coronavirus to actively play on humanity’s fears in an effort to get people to divulge sensitive information about themselves.
This form of phishing attack is not new, however, it’s been very effective, simply because of the human element involved. In this blog, we’re going to show you how hackers and threat actors are actively scouring the news headlines for purely nefarious purposes.
Have You Read?
Email Scams: An Intern's Story
5 Top Features of Office 365 Advanced Threat Protection
Cybersecurity 101: Your End-Users are The First Line of Defence
How Novel Coronavirus is Being Used to Exploit Human Emotions
With the potential for such catastrophic disaster and subsequent tragedy, and with people heralding this as “the new SARS”, Novel Coronavirus has been receiving significant attention in local and global media. Rightfully so, concerns are running high for any loved ones who have either contracted the virus, or been quarantined because of exposure to someone with it.
Unfortunately, these legitimate fears of the population are playing right into the hands of those who would use the tragedy we’re facing to their own iniquitous ends. Hackers and threat actors are seeing this as a way to turn the fear, concern, and curiosity of the general population into something they can exploit to their advantage.
This exploitation comes in the form of an email, claiming to be an alert from the Centers for Disease Control and Prevention (CDC), which has identified new cases of the virus “in your city”. Of course, the email wants you to click on an official-looking link, and when you do, you’ll be taken to a Microsoft Outlook interface that will ask you for your email address and password – as though you are logging into a Microsoft Outlook client.
Here’s an example of the email, as identified by Kaspersky:
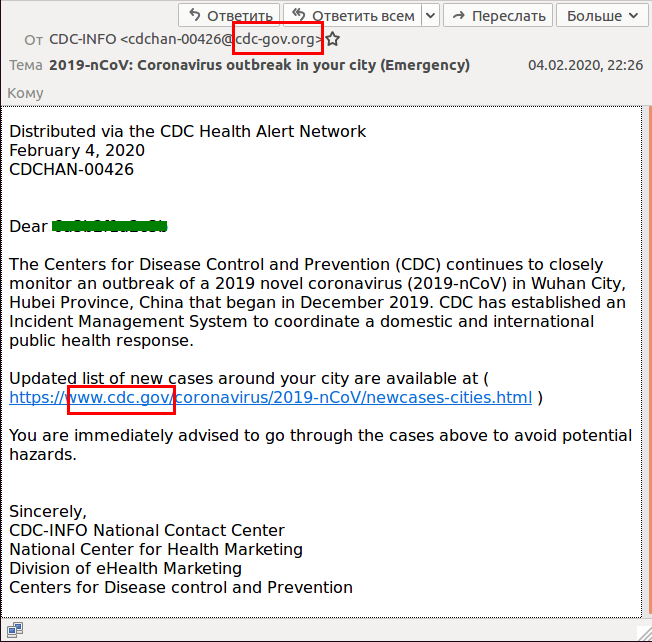
What to Be Aware of in the Novel Coronavirus Phishing Emails
From first glance, this looks like a completely legitimate email. It appears to come from the CDC, it uses medical terminology for the virus in the subject line, and it does talk about the outbreak using predetermined facts (i.e., it began in Wuhan City, it’s been going on for a few months, etc.).
However, as Kaspersky’s article on the subject points out, there are three main issues with this email:
📧 First, the email is sent from someone with the email address that ends in cdc-gov.org (rather than the CDC’s actualgov domain).
🐞 Second, the link in the email is not the actual link that you’re going to be taken to. If you hover over the link without clicking on it, the real address that appears is quite different than what’s showing with the link. This email will not take you to the cdc.gov website.
⚠️ Third, if you actually click on the link, you’ll see that the page it takes you to is not a Microsoft page, although it may appear to be one. However, if you look at the address, you will see that Microsoft’s name doesn’t appear in the link. Of course, this should be a red flag immediately, because there is no reason for any other webpage except for Microsoft’s that should be asking you to reveal your Outlook credentials.
However, if you missed these cues, don’t feel too bad. The threat actors and hackers are using the one word that is designed to make anyone overlook any potential discrepancies and act immediately – the email subject line says Emergency.
That word evokes some strong human emotions. Panic. Fear. If the victim is particularly close to someone who has contracted the virus, it will probably also evoke sorrow, and pain. Conspiracy theorists who see this might be curious enough to click on the link. This range of human emotions is almost guaranteed to throw that common sense out the window.
Prevent Cybersecurity Attacks
Join our Cybersecurity experts as they shares tips and tricks on how to make security the foundation of your organization! Sign up for the Cybersecurity Framework Webinar Series
The Novel Coronavirus Phishing Email Isn’t The Only Example of Exploiting Human Emotions for Nefarious Purposes…
Unfortunately, this isn’t the first time that hackers have used world events that tug at the heartstrings to try and manipulate people into giving away their information. Whenever national or international note-worthy news events take place, especially tragedies, it’s a good bet that threat actors or hackers might try to capitalize on the human emotions.
A recent Secureworld article identified that hackers are most likely to use fear, greed, curiosity, urgency, and helpfulness as the five top exploited emotions in social engineering attacks. And, an infographic released last year targets natural curiosity, high-stress levels, the human desire to help others, and ignorance (or a lack of cybercrime awareness) as the top four major human vulnerabilities used by cybercriminals.

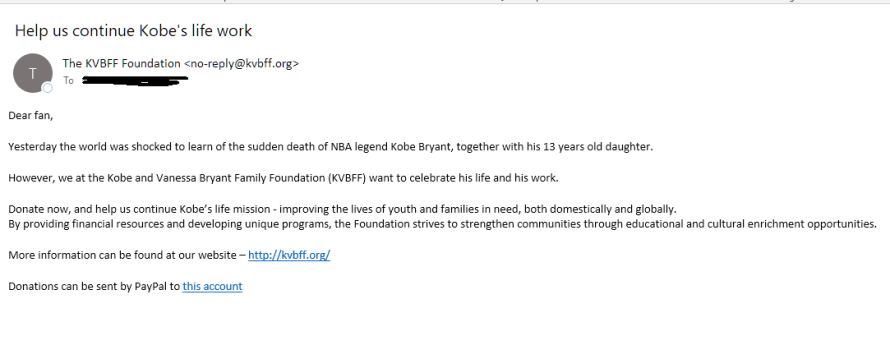
Case in point, another phishing attack that recently exploited a national tragedy centered around Kobe Bryant’s death. In this tactless attack, threat actors and hackers preyed on the grief that sports fans across North America felt at the passing of not only the basketball legend, but of his teenage daughter as well. Phony emails appearing to come from Kobe Bryant’s foundation begged people to help them continue the amazing things that the Bryant family was doing to improve the lives of youth and families in need, and strengthen vulnerable communities around the world.
These emails were supposedly soliciting donations for the Bryant foundation in order to “continue Kobe’s life work”, and the scam email even used the foundation’s legitimate website to create a false sense of security and the illusion of authenticity. However, the threat actors writing the email were asking for people to send donations via PayPal (as seen in the example below), which was, certainly, a separate account that did not have ties to the legitimate foundation.
Protect Yourself from Novel Coronavirus Phishing Emails and Similar Attacks
Both the Novel Coronavirus phishing email and the Kobe Bryant scam email played on humanity’s inherent desire to help others. But, how can you protect yourself from these types of nefarious acts?
According to the Kaspersky article, attentiveness and knowledge are your two best tools to prevent an attack. Question everything that enters your inbox:
- Are there spelling errors in the domain names that are used?
- Does something look a little off?
- Can you verify the domain name of the email address being used?
- Are the links provided actually legitimate links, or when you hover your mouse over the link, does something else pop up?
These questions are a start in determining if the email is coming from a legitimate source, although, if you’re still not sure, it’s best just to be safe and delete the email altogether. Better safe than sorry, as the saying goes!
In addition to this, you can also invest in a tool, like Office 365 Advanced Threat Protection, which can help to detect if the email is fraudulent or legitimate, ensuring that you don’t become a victim of the many threats that are out there today.
Want to learn more about how to protect yourself? Check out our recent Safe Computing & Best Practices on-demand webinar for all end-users, where we discuss some of the most common phishing attacks and how to protect yourself from becoming a victim.
Are you an Office 365 shop? Our Office 365 Security Assessment has been designed to ensure you’re adopting Office 365’s security solutions within your organization. Said solutions can help you increase your security posture and reduce your overall risks, so let us help you! Check out more details here, then contact us and let’s get started!
Tags:
CybersecurityFebruary 18, 2020




Comments