According to an annual report from Interisle Consulting Group, a business and technology strategy firm that regularly publishes reports on phishing activity, the cybercrime known as "phishing" has increased by 61% in the last year, with over 1 million attacks reported. This rise in phishing attacks is a significant threat to internet users globally and requires proactive measures to protect against it.
In this blog, you will find:
🔒 Importance of identifying and avoiding phishing scams
📑 Steps to take if you suspect you’ve been phished
🌈 Protect Your Digital Assets with ProServeIT's Alarm Guardian Managed Cybersecurity Solution
As a Microsoft security solutions partner and specialist, we emphasize that awareness is the first defense against phishing attacks. If you encounter a phishing scam, it is crucial to recognize it immediately. ProserveIT recommends using online security tools like Alarm Guardian, which actively monitors all incoming emails for a potential phishing attempt.
In this blog, we will discuss the basics of phishing scams, including how to recognize a potential scam and what to do if you believe you have encountered one.
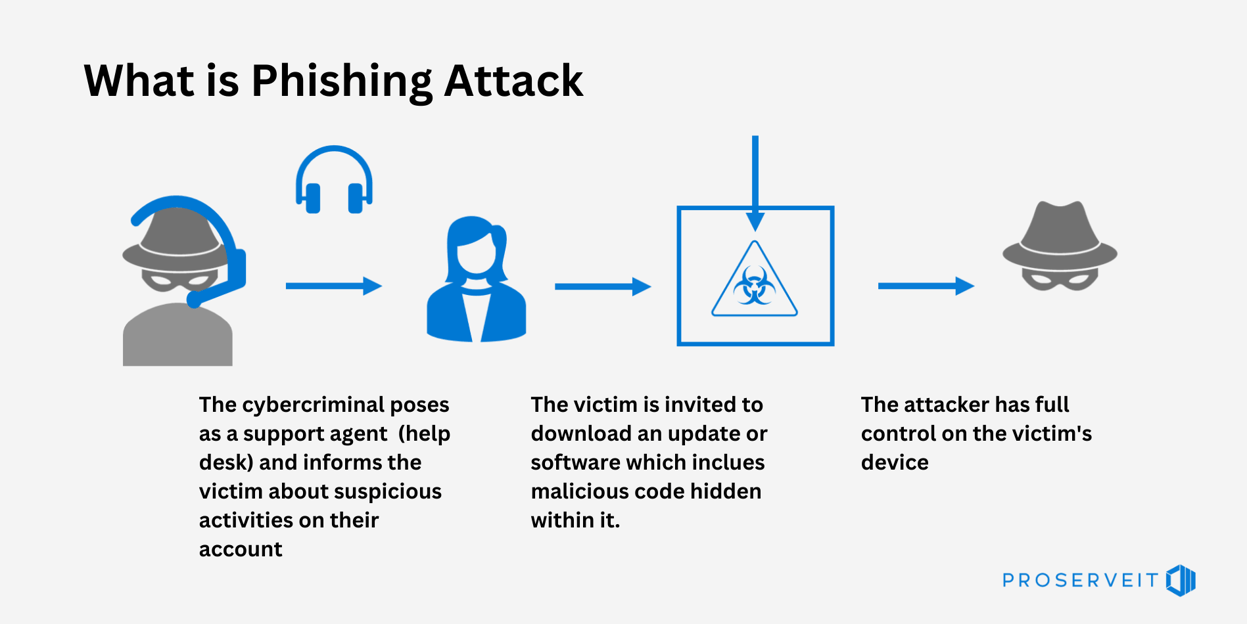
What is a phishing attack?
Phishing is a type of cyberattack where an attacker attempts to deceive and trick a victim into giving up personal or sensitive information, such as passwords, credit card numbers, or social security numbers. This is typically done by sending fraudulent emails, text messages, or instant messages that appear to come from a trustworthy source, such as a bank, social media platform, or government agency.
One of the most common phishing tactics involves a cyber criminal posing as a support agent or help desk, informing the victim of suspicious activities on their account. The victim is then invited to download an update or software that supposedly fixes the issue. However, the update or software contains malicious code hidden within it. Once the victim downloads and installs the software, the attacker gains complete control of the victim's device.
You may be interested in these blogs:
4 Most Common Types of Phishing Attacks
How to Protect Your Organization against Spear Phishing Attacks
5 Best Practices to Protect Your Email Inboxes & Prevent Phishing
Importance of identifying and avoiding phishing scams
By being aware of the risks and taking proactive measures to protect personal and financial information, avoid malware infections, and safeguard businesses and organizations, individuals can stay safe online while using the internet. It's crucial to be cautious of unsolicited emails or messages and verify the sender's or organization's authenticity before providing any personal information. By taking these steps, individuals can avoid the harmful effects of phishing attacks and ensure their online safety.
How to identify phishing scams
As technology advances, so do the methods used by cyber criminals to steal personal information. One of the most common methods used is phishing scams, which can cause significant damage to individuals and organizations alike. Identifying and avoiding phishing scams is crucial to protecting yourself and your personal information.
 Here are some tips to help you identify potential phishing scams:
Here are some tips to help you identify potential phishing scams:
• Check the sender's email address: cybercriminals often use email addresses similar to legitimate ones but with slight variations. Check the sender's email address carefully to ensure it's fair.
• Check/Hover over links before clicking: phishing emails often contain links that lead to fake websites that mimic legitimate ones. Hover over links before clicking to ensure they show to a legitimate website.
• Call to verify: if you need clarification on the authenticity of an email or message, call the person or organization using a verified number and ask to confirm the message's details.
• Do not use your cell phone: it's best to avoid checking suspicious emails on your cell phone, as mobile devices can be more vulnerable to attacks.
• Look for grammatical errors or typos: phishing emails often contain grammatical errors or typos. However, some scams can be sophisticated and have no errors, so this shouldn't be the only indicator.
•Be suspicious of urgent language: phishing emails often use urgent or threatening language to make the recipient act quickly. Be wary of emails that demand immediate action.
• If it's too good to be true, it probably is: phishing scams often promise something too good to be true, such as a large sum of money or a free prize. If it seems too good to be true, it's likely a scam.
• Use technology to help: use anti-phishing tools like Microsoft Defender for Office 365 to help identify and block phishing emails.
Best practices for protecting against phishing scams
Multi-Factor Authentication (MFA) is a security measure used to protect online accounts by requiring users to provide multiple forms of authentication to log in. While Multi-Factor Authentication is an effective security measure to protect yourself from phishing scams, it could be better. Cybercriminals have become increasingly sophisticated in their phishing techniques and are finding ways to bypass MFA protections. Organizations, however, can implement several measures to enhance security and protect against phishing scams that may bypass MFA.
• Azure AD Conditional Access Geo-Fencing applies Conditional Access Policies that restrict users from signing in from specific IP addresses, countries, and locations.
• Device Enrollment into Microsoft Intune is another option that allows Conditional Access Policies to limit the devices that can authenticate and access corporate data.
• Hybrid Domain Join also offers Conditional Access Policies that restrict device access by requiring them to be Hybrid Domain joined.
• Certificate-Based Authentication with Microsoft Defender for Cloud Apps Conditional Access App Control can protect applications by monitoring their sessions.
• Microsoft Defender for Office 365 offers policies that can block phishing emails and add extra protection mechanisms for high-profile C-suite users.
• End-User Awareness Training and Phishing Simulations are crucial in educating users to identify and report suspicious emails as potential threats.
• Alarm Guardian is an added layer of protection that can be used with the above security measures to protect against phishing scams. It combines the power of Artificial Intelligence (AI) with human intelligence to help organizations detect and respond quickly to potential threats. Alarm Guardian provides real-time threat monitoring and alerts, offering an extra layer of security to protect against phishing scams.
Steps to take if you suspect you’ve been phished
If you suspect you have been phished, it is crucial to take action immediately to prevent further damage. Here are some steps to take:
• Reset your password: change your password right away, and make sure the new password is strong and unique. Consider using a password manager to generate and store secure passwords.
• Revoke access: use Azure AD to revoke access to any apps or services that the attacker may have gained access to. This will kick the bad actors out and prevent them from using your account further.
• Check email forwarding: look for suspicious email forwarding addresses that may have been added to your account without your knowledge. Remove any that you did not authorize.
• Disable suspicious inbox rules: check your inbox rules for any suspicious rules that may have been set up to forward or delete emails automatically.
• Check administrative groups: review any administrative groups you may be a part of to ensure that the attacker did not gain additional privileges.
• Review registered devices: check if any additional devices were registered under your account. Remove any that you did not authorize.
• Review sent emails: use Exchange Online Message Trace capabilities to review sent emails and determine if any unauthorized emails were sent from your account.
By taking these steps, you can limit the damage caused by a phishing attack and prevent further unauthorized access to your account.
Protect Your Digital Assets with ProServeIT's Alarm Guardian Managed Cybersecurity Solution
Criminals are getting more sophisticated in their phishing techniques, and organizations must stay one step ahead. Combining multi-factor authentication with enhanced security measures like geo-fencing, device enrollment, hybrid domain join, certificate-based authentication, end-user awareness training and Alarm Guardian can help protect against even the most advanced phishing scams. Additionally, conducting regular security reviews and taking the necessary steps if you suspect you have been phished can help protect your business from further damage. Ultimately, a comprehensive security strategy is key to protecting against phishing scams.
ProServeIT’s Alarm Guardian managed cybersecurity solution can help organizations stay ahead of the curve and protect their digital assets from security threats. Contact us today to learn more about how we can support you in protecting against phishing attacks. ProServeIT is dedicated to keeping your business secure from cyber threats. Let us help get you the protection you deserve.
Tags:
Cybersecurity.webp?width=50&height=50&name=Hyun%20Blog%20(1).webp)
May 04, 2023





Comments