As cyber risks continue to evolve, making and using a comprehensive security operations programme is important to keep your network safe. A holistic method combines efforts to prevent, detect, analyze, and respond. This gives you the most protection possible.
Assessing and figuring out your organization's information security risk tolerance level and making an information risk tolerance model are important parts of building a comprehensive security operations plan. With this step, you can protect your organization in an effective and efficient way.
In this blog post, we'll talk about the benefits of using an information risk tolerance model and give you tips on how to build one for your business.
In this blog, you will find:
❓ What is Security Risk Tolerance?
🔐 Why is a Formal Information Security Risk Tolerance Metric Essential?
⭐ Benefits of having a Clear Risk Tolerance Definition
❔Determining Your Information Security Risk Tolerance Level: Asking the Right Questions
What is Information Security Risk Tolerance?
Information security risk tolerance is a metric that indicates the degree to which your organization requires its information to be protected against confidentiality leaks or compromised data integrity.
Why is a Formal Information Security Risk Tolerance Metric Essential?
This knowledge is critical for striking the right balance between overprotecting data (resulting in overspending) and under protecting it, potentially failing to meet the organization's needs and requirements.
The key to gaining this vital knowledge lies in consulting your senior management to understand their expectations regarding information protection. The conversation should include a discussion around the fact that not every piece of data requires protection, and not all important data should be protected at the same level.
By engaging with your senior executives, you can establish reasonable data protection standards that align with your organization's information security risk tolerance level. The goal is to determine which protection practices fall within the risk tolerance level and which exceed the level of risk the business is willing to accept.
-
Benefits of a Clear Risk Tolerance Definition
By the very nature of doing business, every organization has some form of a risk tolerance model. It may be a formal document, an ad-hoc undocumented process, or something in-between, but a formally documented process offers several advantages:
-
👁️🗨️ Provides a clear definition of the organization's risk tolerance and assigns ownership of specific risks
-
🕵️ Identifies and quantifies risks based on risk levels and exposure
-
🛡️ Ensures a consistent and proactive approach to risk management rather than a reactionary one
-
Bridging the Gap in Threat Response
Using an ad-hoc, informal approach might save time initially, but it can leave gaps when dealing with threats. This method depends on a senior manager learning about potential or active threats case-by-case and then giving the okay for the risk to be assumed. This creates a reactive process that isn't consistent and may leave some risks not properly examined.
In contrast, having a formal information security risk tolerance document helps you know what actions should be taken for each identified risk type and who in your organization is responsible for making sure the risk is handled in the approved way. There's no guesswork here, as the document is clear, and the information has been approved by senior management.
Determining Your Information Security Risk Tolerance Level: Asking the Right Questions
Determining a realistic information security risk tolerance Level will require thoroughly examining your organization’s business risks. However, there's no need to evaluate specific threats or vulnerabilities to determine your information risk tolerance level.
The key is to ask the right questions about your organization’s risks. This is crucial because many organizations fail to understand their risk tolerance levels due to asking the wrong questions.
For example, asking the question, “What kinds of threats do the organization consider acceptable (or unacceptable)?” seems like a logical starting point. However, this is the wrong question to ask.
Risk tolerance is a tool that must apply universally to all threats. By asking the above question, you unnecessarily narrow your field of view by defining your risk tolerance using specific threats. Since we cannot accurately predict what an attacker might do, there is a risk in itself that an unforeseen attack will cause unexpected damage.
So, what is the right question to ask? Ask your organization:
❓ What kinds of business impact could we accept? (And how often could they happen?).
Why is this the right question to ask? Here are 4 reasons:
- ✅ When defining a risk tolerance level, you want a definition that can be consistently applied, regardless of the project, threat, vulnerability, or time.
- ✅ Using a business-centric approach to risk tolerance emphasizes the impact on the business as the main determinant of whether a risk is acceptable or not.
- ✅ Threats and vulnerabilities that organizations face change almost daily, but the business impact you're willing to tolerate is consistent over time.
- ✅ This approach aims to define risk-framing assumptions for potential impact created by security incidents, supporting a common method for risk tolerance decisions
- In conclusion, understanding your organization's information security risk tolerance level is crucial for effectively managing business risks and making informed decisions about implementing resource allocation and security measures.
- By focusing on the business impact instead of specific threats and vulnerabilities, your organization can develop a more resilient and adaptable security strategy that can respond to changes in the threat landscape.
-
Partnering with a team of highly experienced security experts is the most cost-effective and efficient way to define your organization's information security risk tolerance level and to implement an information risk tolerance model.
-
This collaboration will equip your organization with a list of defensible risks, clear responsibility, accountability for defining risk tolerance, and the ability to leverage the quantified risk tolerance level in broader risk assessment management activities.
We Can Help You Understand Your Risks
Don't wait until your organization becomes the victim of a cybercrime.
Engaging with our team of experienced security experts at ProServeIT will help you define your risk tolerance levels and develop a tailored approach that addresses your organization's unique needs and requirements.
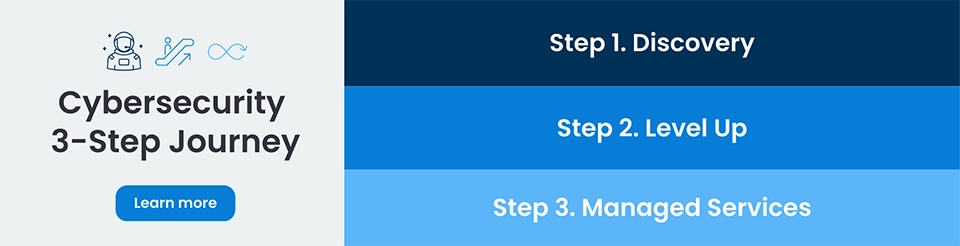
The Power of ProServeIT's Cybersecurity 3-Step Journey 🚀
Step 1: Discovery - Understanding Your Starting Point
The first step in ProServeIT's cybersecurity journey is discovery. Understanding where an organization should start is critical to ensuring a return on investment from its security practices. With ProServeIT's expertise, organizations can be confident that they have a clear understanding of their starting point and can begin to take the necessary steps to secure their digital assets.
Step 2: Level Up - Improving Your Security Practices
The next step in the journey is to level up an organization's security practices. With the starting point understood, ProServeIT can help organizations implement new security measures and improve existing ones to protect their digital assets and reduce the risk of cybercrime.
Step 3: Managed Services - Evolving Security Practices
Security is an ongoing process that needs to evolve as the business grows. ProServeIT offers managed services to ensure that an organization's security practices are always up-to-date and effective. With ProServeIT's expertise and experience, organizations can be confident that their security practices will continue to evolve to meet the changing needs of their business.
Tags:
CybersecurityApril 18, 2023




Comments