The evolution of the cyber threat landscape has forced organizations to think differently about security operations. A holistic approach to security operations is critical in today’s advanced threat landscape. A holistic approach means combining prevention, detection, analysis and response efforts. It does not matter whether you are a small business or a global enterprise. Your data is valuable to cybercriminals. You are not an exception.
With the increasing sophistication of attacks and the threat of stolen information and ransomware (think the recent WannaCry incident – for more details about WannaCry, refer to our previous blog post “WannaCry Ransomware– Immediate Actions to Take & 7 Best Practices Moving Forward”), it’s vital that you take a new approach to defend your network from the many cybercriminals out there.
We have noticed that many organizations are struggling to defend against and prevent threats while juggling business, compliance, and consumer obligations. The increasing prevalence of public data breaches is highlighting the importance of proactive defensive measures. Threat management has become resource intensive, requiring continuous monitoring, collection, and analysis of massive volumes of security event data.
This is why it is important to take the holistic approach to security operations and work with experts to have a solid plan in place. Using traditional anti-virus/anti-spam/malware protection software is simply not enough. The first step in building your holistic Security Operations Program is to assess your current environment. We can run a simple security assessment for you so that you can learn your organization’s current security status. Get in touch with us today to get your assessment done!
Want more information about Security Operations Program? Read along!
What is a Security Operations Program? Combination of prevention, detection, analysis & response efforts
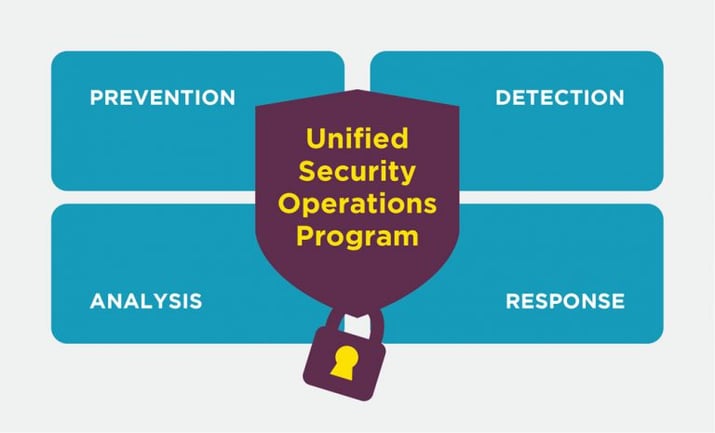
Security operations is no longer a centre, but a process. The need for a physical security hub has evolved into the virtual fusion of prevention, detection, analysis and response efforts. When all four functions operate as a unified process, your organization will be able to proactively combat changes in the threat landscape.
Why have a holistic Security Operations Program?
A holistic Security Operations Program actively transforms security events and threat information into actionable intelligence, driving security prevention, advanced threat detection, more rapid analysis of threats to both your network and your business, and the response process.
Data breaches have caused many headaches to companies like Target where the theft of a large amount of personal customer data damaged Target’s reputation. There were also tangent costs as Target had to pay to set up credit monitoring for every customer whose data was stolen.
Cybercriminals are at war with your organization. You need to have a battle plan to defend yourself. Security and information management alone will not provide you with the defence you need. All you will have is a reactive response that may or may not prevent any serious damage.
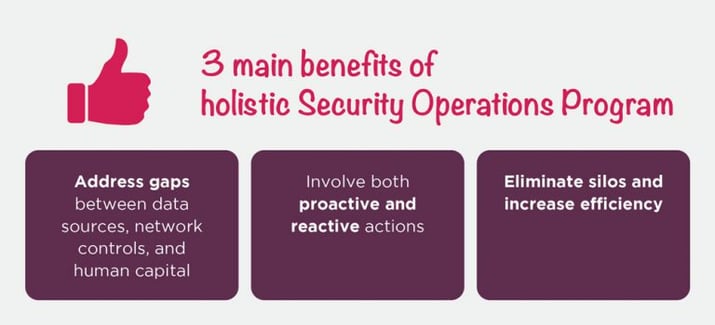
Here are the benefits of a unified Security Operations Program and the ways it addresses the challenges of the traditional security operations centre:
- Address gaps between data sources, network controls, and human capital
Traditional legacy Security Operations centres fail to address the gaps between data sources, network controls and human capital. There is limited visibility and collaboration between departments, resulting in siloed decisions that do not support the best interests of an organization at large.An integrated Security Operations Program allows you to identify threats earlier, focus efforts on the most dangerous threats, and prioritize threat indicators to rapidly identify potential events.
- Involve both proactive and reactive actions
A Security Operations Program takes into account your big picture and arms you with a battle plan that involves both proactive and reactive actions. Prevention, detection, analysis and response processes will contextualize threat data to supplement each other.Executives can understand relevant threats and allocate needed resources where necessary, and improved communication with top executives about risks to the business, ROI in security, and probable actions of adversaries in the future.
- Eliminate silos and increase efficiency
This collaboration of prevention, detection, analysis and response processes eliminates siloed decisions by connecting people, processes and technologies. You’ll have less room for error, consume fewer resources and improve operational efficiency with a transparent Security Operations Program.Improved situational awareness (focusing on attackers’ tactics, tools and procedures), reducing incident response time by conceptualizing incidents, and increasing operational efficiency in terms of asset and human capital management.
In summary, here are short term and long term benefits you will get out of a unified Security Operations Program:
Short term, your Security Operations Program will streamline the process of formalizing a unified Security Operations Program tailored to your organization-specific needs. You can assess current operational gaps and begin to develop your unique implementation process in a structured manner.
Long term, your Security Operations Program will give you greater visibility into your immediate threat environment, improved effectiveness of internal defence controls, increased operational efficiency and collaboration between prevention, detection, analysis and response efforts, and ultimately an enhanced security pressure posture.
How do you build a Security Operations Program? Build your own with ProServeIT!
This is where ProServeIT comes in. Building an integrated Security Operations Program should not be a short-term strategy. A Security Operations Program is something your organization will maintain for a long time. It needs to be effective for your business and cost efficient. So we recommend you take the time to build it with an expert’s help. ProServeIT’s experienced security team has worked with many organizations, both big and small, in various industries to help them build a solid Security Operations Program. Here is the summary of a 4-step approach we take with our customers:
- Step 1. Access and audit the current environment to have a complete understanding of how your business operates and the potential cyber threats you face. This information will form the foundation of your Security Operations Program.
- Step 2. Once we have a full understanding of your current IT environment and potential risks and threats, formalize the standards and processes of your Security Operations Program and tailor them to your organization.
- Step 3. Develop a strategy to incorporate intelligence into your Security Operations Program such as incident response and vulnerability management (including indirect consequences in the aftermath of an incident).
- Step 4. Determine the templates and tools you need to facilitate the improvement of your security operations. Streamline your security prevention, detection, analysis and response processes. Develop an effective maintenance and optimization of your security operations and procedures. And communicate the new tools and processes with end users and provide the appropriate trainings for them.
This is a basic framework and each step involves various tasks. The tasks involved in each step are different from one organization to the other because every organization and its needs are different. Let’s connect. The first step for us is always getting to know your organization, your current IT environment, and what is important to you as an organization moving forward. Get in touch with us to first get a security assessment done to see a complete picture of your organization’s security status. Have questions and simply want to get more information instead? We are here for you! Use the form below to reach out to us. We will get back to you within one business day, guaranteed!
Tags:
CybersecurityJune 06, 2017



Comments