If you are a non-IT professional, please read along. This post is for you! If you are an IT professional, please click here to read the blog post written for you.
On Friday, May 12, 2017, a ransomware variant titled “WannaCry” infiltrated several UK-based National Health Service locations. Since then, it has spread across 200 countries and infected more than 200,000 endpoints.
WannaCry is a ransomware variant that targets unpatched Windows operating systems (Windows XP, 8, Vista, 7, 2012, 10, and Server 2003). Infected users experience file encryption in exchange for a $300 bitcoin ransom. We will discuss in more detail later in this post but the bottom line is that paying the ransom does not make sense in most cases. Do NOT pay unless absolutely necessary! Talk to an expert first before taking actions.
It is important to note that you are still vulnerable if you are running supported versions of Windows. Just because a patch is available does not mean you are secure. Ensure your systems are patched and up to date.
Let’s first discuss what immediate actions are required at the moment for both scenarios: 1) if you have not been infected; and 2) if you have been infected. And we will suggest the 7 best practices moving forward.
Immediate Actions to Take
- If you have not been infected
Patch or Inoculate OS
Determine your exposure and the potential risk implications – identify and document outdated windows operating systems.
Back Up Your Data
Make the time to back up all critical data to the cloud and/or to an external hard drive.
Communicate
Send internal alerts to educate employees on the WannaCry threat campaign and external alerts to clientele
Threat Intelligence
Review your threat intelligence program and ensure that they are being consumed and actioned. Timely intelligence can give you a crucial head start against threat actors.
Incident Response
Formalize incident response procedures. Create detailed runbooks that actively address all mitigation and operational procedures in the event that an endpoint is infected.
- If you have been infected
Shut Down
Shut down and disconnect any infected systems as part of your overall risk mitigation strategy.
Don’t Pay
After evaluating all possible outcomes – if you become infected, payment should not be an option.
Analyze the Scope
Determine exactly how much of your network has been infected and how many files have been compromised.
Communicate
Organizations that have fallen victim to a ransomware attack are encouraged to work with their local law enforcement office and send internal alerts to educate employees on the WannaCry threat campaign.
Locate Backups and Restore Data
Have you shared the data with someone else using a cloud-based storage service like OneDrive, Google Drive, or Dropbox? Even if the data is encrypted, these services will often allow you to revert your files to a previous state.
- Bottom-line: Do NOT pay unless it is absolutely necessary! Talk to an expert first!
A cost-benefit analysis can easily tell you what you should do when it comes to ransomware. We live in the real world and often we work for companies looking to maximize their profits. It is practical for them to perform a risk-based cost benefit analysis to determine whether to pay or not. To pay or not should be a business decision based on which option is most cost effective.
Consider these variables:
- What is the potential harm caused from losing that data or system? Is the data or system critical in nature? Are there adequate backups and a recovery process to minimize interruptions?
- What is the relative cost associated with paying? Most ransom demands are meant to be reasonable to incite you to pay.
- What is the probability that your data will be decrypted? An “unethical” extortionist could receive payment and choose not to decrypt your data.
- What is the probability that once you pay, you may be extorted in the future? An attacker could leave malware on your systems in the form of a backdoor, which they could use to compromise you for additional ransom. An attacker could also spread the knowledge that you are willing to pay, inciting other cybercriminals to attack you.
These considerations result in the conclusion: DON’T PAY unless it is absolutely necessary. For most cases, paying the ransom does not make sense. It is the unequivocal recommendation from authorities and ProServeIT that you do not pay unless absolutely necessary. Payment should NOT be your first action. Talk to an expert first to examine and explore possible options.
7 Best Practices Moving Forward
- Just because a patch is available does not mean it has been deployed.
Many organizations run a few patching cycles behind. Conduct an inventory of current operating systems and immediately patch vulnerable endpoints. Stay up to date with your patching efforts, and ensure other vulnerability management practices.
- Take a proactive approach to vulnerability identification.
Leverage third-party open-source vendor websites and mailing lists to actively search for new indicators of compromise and CVEs. Schedule regular scans and prioritize your patching efforts.
- Get in the habit of periodically backing up all sensitive data.
Whether through cloud-based solutions or via external hard drives, sensitive data must be frequently backed up and stored in a secure manner.
- Use this incident as leverage to increase awareness.
The WannaCry incident can be leveraged not only to create organizational situational awareness around security initiatives, but also to drive adoption of foundational security measures such as patch management, threat intelligence, and zero-day mitigation policies, procedures, and solutions.
- Consider disabling unused legacy protocol
Assess port security and exposure of internet-facing services related to affected RDP and SMB services. Standard ports include 139 and 445. Consider disabling unused legacy protocol such as SMBv1.
- Formalize incident response procedures.
Create detailed runbooks that actively address all mitigation and operational procedures in the event that an endpoint is infected. Actively distribute runbooks and collaborate internally so that all security members are aware of the required steps and procedures.
- Maintain a holistic security program
WannaCry is a good reminder that security threats are often unknown and unpredictable. The only way to maintain effective defense is through a comprehensive and flexible security program.
Prevent: Defense in depth is the best approach to protect against unknown and unpredictable attacks. Effective anti-malware, diligent patching and vulnerability management, and strong human-centric security are essential.
Detect: There are two types of companies – those who have been breached and know it, and those who have been breached and don’t know it. Ensure that monitoring, logging, and event detection tools are in place and appropriate to your organizational needs.
Analyze: Raw data without interpretation cannot improve security, and is a waste of time, money, and effort. Establish a tiered operational process that not only enriches data but provides visibility into your threat landscape.
Respond: Organizations can’t rely on an ad hoc response anymore – don’t wait until a state of panic. Formalize your response processes in a detailed incident runbook in order to reduce incident remediation time and effort.
Let us Help!
Being proactive to have a holistic security program in place is becoming more and more critical to stay productive. ProServeIT has worked with numerous organizations in all sizes and industries. Whether you need backup solutions, a disaster recovery solution, or a consultation to learn more about ways to protect your organization, we are here to help. Whatever your needs are, we will work with you and provide you with the customized guidance to help protect your organization from ransomware attacks!
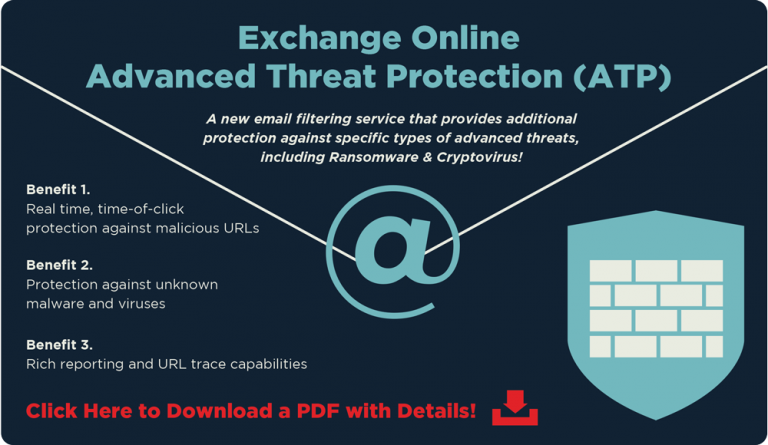
Want more information about how we can help you before chatting with us? One of the recommendations we suggest to our customers is to leverage tools such as Advanced Threat Protection (ATP) to protect from suspicious emails and pop-ups. Click the image below to download a one-pager with details.
Tags:
CybersecurityMay 30, 2017



Comments