Did you know that 66% of Malware was installed via malicious email attachments and 91% of Cyberattacks started with a phishing email?
As a Solutions Partner with Microsoft, ProServeIT, is well-versed in ransomware prevention and have the experience, tools, and processes needed to protect organizations from ransomware attacks. This blog will discuss what is a ransomware, different types of Ransomware attacks and how to protect your organization from malicious threats.
In this blog, you will find:
😈 What is a ransomware attack?
🌪️ Ransomware as a service (RaaS) and its impact
🔏 How to protect your operating systems from ransomware
🛡️ Alarm Guardian: ProServeIT’s Security Operations Center
👨🏫 ProServeIT Academy: Cybersecurity Course
What is a ransomware attack?
Ransomware is a type of malware which restricts access to the computer system that it infects and demands a ransom be paid to the creator(s) of the malware for the restriction to be removed.
Some forms of ransomware encrypt files on a system's hard drive, while some may simply lock the system and display messages intended to coax the user into paying.
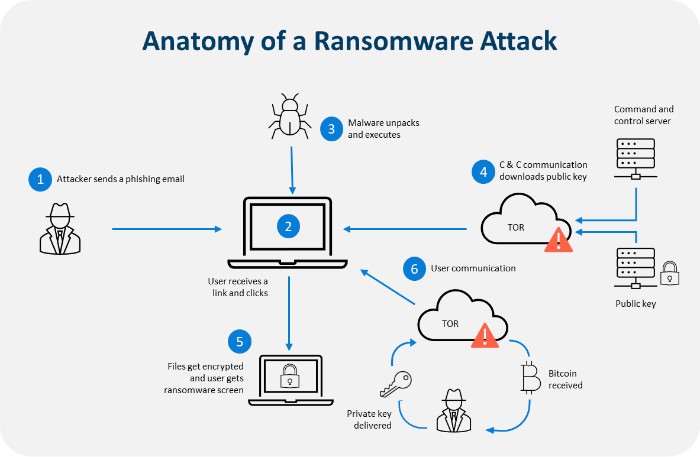
Why are ransomware attacks growing?
Ransomware attacks are becoming more sophisticated and frequent. Attackers often target organizations with small security budgets or those that are not adequately protected against such threats. They use various techniques to gain access to the system, such as exploiting vulnerabilities in software or using phishing emails. Once they gain access, they can deploy ransomware to encrypt files and demand ransom payments in exchange for unlocking the files.
The growth of ransomware attacks is due to hackers’ understanding of the financial incentive associated with ransomware. As a result, attackers are targeting organizations as they know that businesses are more likely to pay a ransom to get their data back, rather than lose it forever.
How do I get ransomware?
There are common myths regarding ransomware that can mislead many people to believe they are safe from it but an organization of any size can be “targeted” by a ransomware attack.
It is essential to be aware of the common ways ransomware can enters a system:
✉️ Malicious Emails: malicious emails can be sent with malicious attachments or links that, when opened, will install malware on the system.
🌐 Infected Websites: attackers can exploit vulnerable websites and inject malicious code into them that can download ransomware and install it on a user’s computer.
💾 Drive-by Downloads: attackers can create malicious websites designed to download ransomware automatically when the website is visited.
🏧 Compromised Accounts: hackers can use compromised accounts or stolen credentials to login and take control of the system, allowing them to deploy ransomware.
You may be interested in these blogs:
Ransomware Attacks Impact Organizations of All Sizes: 3 Common Myths
The Emotional Impact of Ransomware: What It Feels Like to Be A Victim
Why To Have A Backup Plan & Disaster Recovery Plan for Small Business
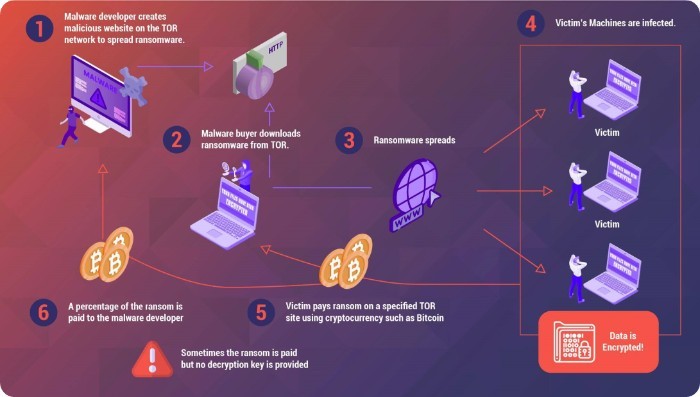
Ransomware as a service (RaaS) and its impact
Ransomware-as-a-Service (RaaS) has emerged as one of the fastest-growing cyber threats in recent years. RaaS is an arrangement between an operator and an affiliate. The RaaS operator sells access to the ransom payload and decryption details to an affiliate, who performs the intrusion and is responsible for deploying the actual ransomware. By using RaaS, attackers can quickly and easily launch malicious campaigns aimed at extorting money from victims. What is unique about the RaaS is the amount of automation used while leveraging cloud computing.
The impact of RaaS is vast, as it provides an easy way for any attacker to quickly launch a ransomware attack with minimal effort and risk. RaaS can be used to target anyone from small businesses to large enterprises, making it a major threat in the cybersecurity landscape. Additionally, RaaS makes it easier for attackers to spread ransomware quickly, as it can be installed remotely without physical access to the target system. Ransomware attacks also come with a heavy price since attackers are able to lock down networks and lock out users until they pay the ransom.
How to protect your operating systems from ransomware
Ransomware is a serious threat and can have devastating consequences for businesses of all sizes. It’s important for organizations to execute best practices to protect themselves against ransomware by educating their employees, creating a rigorous backup plan, disaster recovery strategy and using advanced security technologies.
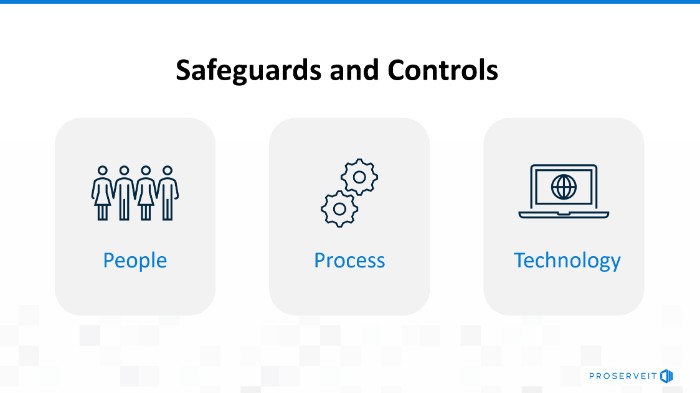
People
Define an Information security Policy that internal and external parties communicate, read, understand, and acknowledge.
Security Awareness training & employee education should be conducted regularly to ensure that personnel know the potential risks associated with ransomware and how to identify malicious emails, links, attachments, and websites.
Defined Roles and Responsibilities can help ensure that everyone is aware of their responsibilities when it comes to cybersecurity and can help prevent a ransomware attack by limiting access to sensitive data and systems.
Segregation of duties is an important security control for organizations, as it requires the inputter and authorizer to be separate entities to reduce the risk of a single user carrying out unauthorized activities that could lead to a ransomware attack.
Disciplinary Actions
can help prevent ransomware attacks by encouraging employees to remain vigilant when it comes to cyber threats.
Process
Developing and Implementing a Cybersecurity Strategy roadmap that defines the roles and responsibilities of employees, outlines risk mitigation measures and implements disciplinary actions for malicious behaviour
Implementing security standards and frameworks applicable to your industry, such as ISO 27001, PCI DSS, Cybersecurity Framework, ISO 22301, PIPEDA etc.
• Measure third-party compliance against the standards mentioned above
• Regularly conduct third-party security assessments – at least annually
• Define a charter for all standards implemented
• Regularly conduct vulnerability assessment – At least quarterly.
Regularly conducting Penetration Testing either biannual or annually.
Establishing a change management process/committee
Reviewing security event logs and user access allow organizations to monitor system activities, detect suspicious behaviour, and quickly mitigate threats such as ransomware.
Technology
Secure Backup and Recovery means backing up data securely and conducting data recovery tests regularly.
Encryption and Key management: encrypt sensitive data in use, in transit and at rest.
Application, Cloud & System Hardening
Security patches must be regularly deployed across the enterprise within the month of release by OEM (Original Equipment Manufacturer),
• Block Remote IT management tools such as Teamviewer, Splashtop, Remote Manipulator System, Anydesk, Atera Remote Management, and ngrok.io via network blocking, such as perimeter firewall rules, if not in use in your environment. If these systems are used in your environment, enforce security settings where possible.
• Integrate security into your Software Development Life Cycle (SDLC)
• Uninstall unnecessary applications and implement application control
Zero Trust and Network segmentation: Develop and implement a Zero-Trust strategy, especially at all third-party connections and segment systems that store or process sensitive data from the rest of the network.Conclusion
Ransomware is a serious threat and can have devastating consequences for businesses of all sizes. It’s important for organizations to take steps to protect themselves against ransomware by educating their employees, creating a rigorous backup plan, having a disaster recovery strategy and using advanced security technologies. By understanding the risks associated with ransomware and taking the necessary precautions, organizations can reduce the likelihood of a ransomware attack and mitigate its impact.
Alarm Guardinan- ProServeIT’s Security Operations Center
As a certified Microsoft Solutions Partner for Security, ProServeIT can help you monitor and improve your organization's security posture while preventing, detecting, analyzing, and responding to cybersecurity incidents around the clock.
ProServeIT’s Alarm Guardian managed cybersecurity solution is, in essence, your Security Operations Centre, taking on the burden of constantly monitoring your environment for potential threats.
Using Microsoft Sentinel as the monitoring entity, our cybersecurity team, working 24 x 7 x 365, ensures that your environment is always protected. If any suspicious activity is detected, we’ll take action to protect your environment and eliminate potential threats.
ProServeIT Academy: Cybersecurity Course
Are you curious about the potential of Artificial Intelligence (AI) in cybersecurity, but also concerned about the potential risks? Join us for an enlightening session where we'll dive deep into the good and bad of AI in cybersecurity. From its ability to quickly detect and respond to cyberthreats to its potential for misuse, this class will provide you with a comprehensive understanding of the impact of AI on cybersecurity. We’ll share a real-life scenario to illustrate what can happen. cyber threats
Whether you're a business owner, IT professional, or just someone who wants to stay informed, you won't want to miss out on this opportunity to learn from experts in the field. So, mark your calendar, and get ready to explore the exciting and ever-evolving world of AI in cybersecurity.
Register for the class here.
Tags:
CybersecurityMarch 06, 2023





Comments