As today’s cybersecurity landscape has been drastically changing, organizations need to address cyber threats with a new approach. Due to the complexity of the cyber threats, a holistic approach – rather than ad hoc responses – is necessary. A holistic Security Operations Program involves prevention, detection, analysis, and response efforts and as all four functions operate as a unified process, your organization can proactively combat cyber threats.
The incident response of most organizations is though still ad hoc, at best. A formal management plan is rarely developed or adhered to, resulting in ineffective firefighting responses and inefficient allocation of resources. One of the reasons has been a lack of support from senior managements. Security was a topic that C-level executives almost turned the other cheek to, and now we’re seeing a spotlight turned directly on it. The Ponemon Institute (an American cybersecurity think tank) predicted in its report, “2015 Global Megatrends in Cybersecurity,” that increased interest in security from C-level executives will be only growing in significance in the coming years.
Security incidents are inevitable. Inefficient use of time and money when retroactively responding to incidents, negatively affecting revenue and workflow of the business. The first step in building your holistic Security Operations Program is to assess your current environment. Get in touch with us so that we can run a simple security assessment for you. This will give you a complete picture of your current security status.
What we are going to focus on in this post is how to measure the success of the holistic Security Operations Program. Your senior management is aware of the importance of data security and is willing to invest in a comprehensive Security Operations Program. But they will want to have hard evidence of effective security processes and compliance efforts. How can you provide it? The answer is metrics.
Security Metrics – 3 Main Reasons Why You Should Measure Them
Metrics are measurements that are compared to a baseline. Metrics help you determine what is working well and what needs improvement within your security policies, processes, and technology. While the raw data offers insights to you as an IT/security professional, the key is to find important correlations on how it can apply to the business as a whole. It’s all about context. For example, metric = reduced # of incidents last year. The business correlation is the increased overall security in addition to reduced interruptions to customer service time, which means overall improved business performance.
As security becomes a priority, IT and security leaders need to establish more business-friendly methods to present pertinent security-related information to the senior management. Metrics, tangible data points extracted from your hardware, software and security devices, provide basic insights based on past data that the senior management can relate to and find useful.
Here are 3 major benefits that metrics can offer you and your senior management:
📊 1. Metrics assuage executives’ fears
Metrics help executives (and IT/security professionals) feel more at ease with where the company is security-wise. Security metrics help identify areas for improvement and gaps in the organization’s security posture that can be filled. A good metrics program will help identify deficiencies in most areas, even outside the security program, helping to identify what work needs to be done to reduce risk and increase the security posture of the organization.
📊 2. Metrics answer executives' questions
Numbers either help ease confusion or signify other areas for improvement. Offering quantifiable evidence, in a language that the business can understand, offers better understanding and insight into the information security program. Metrics also help educate on types of threats, staff needed for security, and budget needs to decrease risk based on management’s threat tolerance. Metrics help make an organization more transparent, prepared, and knowledgeable.
📊 3. Metrics help to continually prove security’s worth
Traditionally, the security team has had to fight for a seat at the executive table, with little to no way to communicate with the business. However, the new trend is that security is being invited before they have even asked to join. This trend allows the security team to better communicate on the organization’s security posture, describe threats and vulnerabilities, present a “plan of action,” and get a pulse on the organization’s risk tolerance.
5 Tips for Implementing a Successful Security Metrics Program
Security metrics are difficult to quantify. Many organizations and subject matter experts recognize the difficulty of establishing and maintaining an effective metrics program. This results in challenges when explaining security concerns and an inability to acquire senior management’s support for changes or additions needed for the security technology program.
In a resource-constrained environment, availability of additional resources for investment could be limited in the absence of solid evidence. Metrics allow the organization to understand its current risk posture and support initiatives to reduce those risks.
So how can we successfully implement a security metrics program? Although implementing and maintaining a security metrics program may seem like a daunting task, there are some guidelines and tips that can help you with the process.
👓 1. Don’t overwhelm yourself by trying to measure everything at once. Prioritize the metrics according to your organization’s specific maturity and risk tolerance, as well as a cost/benefit analysis of each potential metric.
📈 2. Develop a growth plan as your organization and its metrics program mature, so you can continue to optimize it.
💬 3. Communicate the results effectively. Be prepared to present the metrics that truly matter to executives rather than confusing them with unnecessary data. Pay attention to metric accuracy and reproducibility. No management wants inconsistent reporting.
📅 4. Work with a team of security experts. According to the same Ponemon Institute report, 67 percent of the participants believe that there is a knowledge gap and they need more knowledgeable and experienced cybersecurity practitioners. Working with a team of highly experienced experts is the most efficient way to address this challenge. Talk to us to get more information.
🔒 5. Use the relevant results from your metric analysis to help create an Incident Response Plan. If you work with a team of security experts, they produce this Plan for you.
How you can use Azure Sentinel to proactively find and destroy threats in your environment
Why is an Incident Response Plan Beneficial to Your Security Metrics Program?
Once you have specific Metrics about the type of cyber threats and attacks you are facing, the next step is to create an Incident Response Plan. This is where your threat metrics and analysis can become an actionable plan to respond to occurring incidents.
The success of a metrics program is largely due to understanding the difference between quality and quantity. Attempting to measure anything and everything is not an efficient use of staff time and creates the potential for inconsistent measurements. For the most efficiency, devote your time to knowing what metrics will be provided to your organization, as well as assurance of their relevance, reliability, and reproducibility.
In the short term, an effective Incident Response Plan will streamline an incident management program that is customized to your organization’s needs. Long term, your Incident Response Plan will help you minimize any damage from an attack. As incidents are properly tracked, analyzed, and handled per a well-defined process, potential breaches will be reduced to minor incidents.
Here are 3 additional benefits of an Incident Response Plan:
🛡️ 1. An Incident Response Plan documents how your organization responds to actual cyber attacks. It establishes your detection methods, what is done once an attack is detected, who is notified, how an attack is remediated, and how the attack is recorded and communicated to relevant staff.
🛡️ 2. An Incident Response Plan makes every member of an organization accountable in some way to the overall threat defense of the company. Whether end users, cyber security staff or executives, the Incident Response Plan outlines the roles and responsibilities everyone has in combatting incidents.
🛡️ 3. An Incident Response Plan provides a method for retaining knowledge gained during an attack. Lessons learned are recorded and then disseminated to ensure people aren’t reinventing the wheel each time an attack occurs.
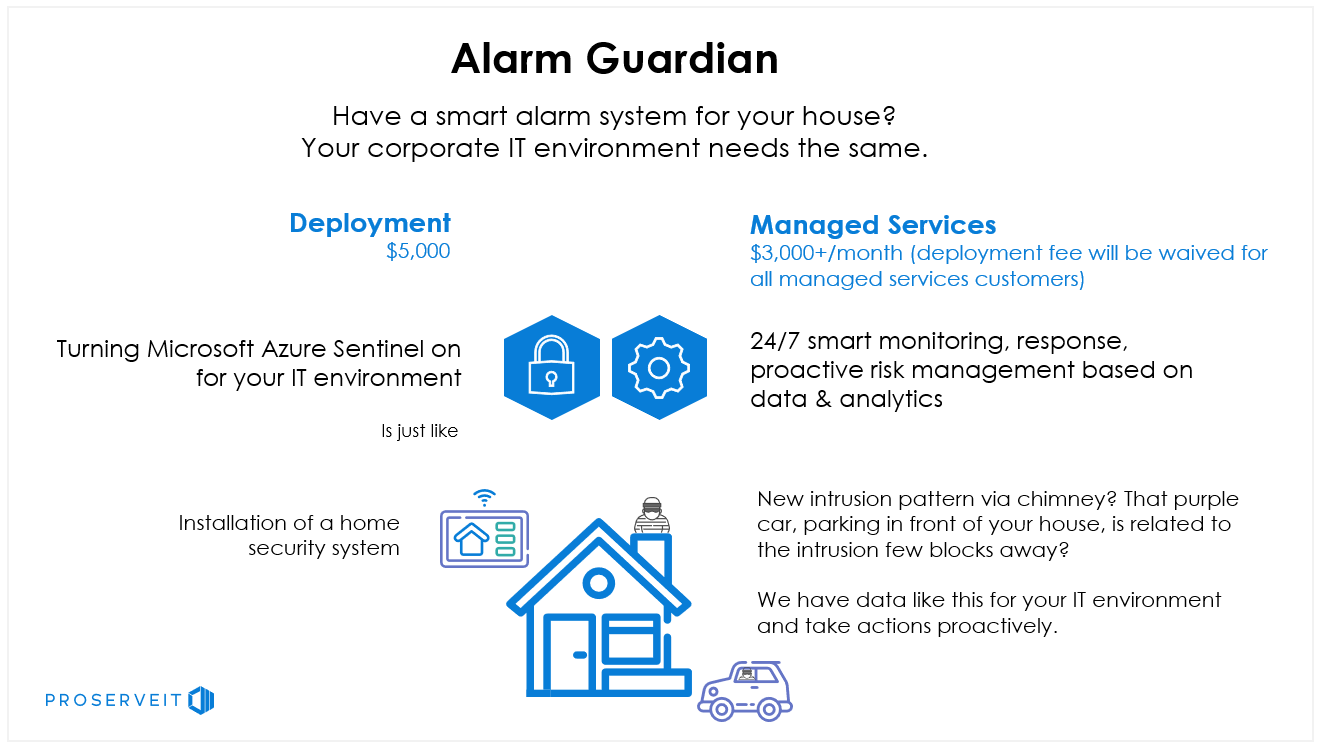
Ready to Protect Your Digital Assets with ProServeIT's Alarm Guardian Managed Security Solution?
If you’re looking for ways to increase your security posture and protect your digital assets in a cost-effective and efficient way, then ProServeIT’s Alarm Guardian could be the exact managed security solution you’re looking for.
ProServeIT’s Alarm Guardian:
☑️ Includes the installation of your new digital “security system”, so that you can protect your digital assets.
☑️ Proactively monitors alerts that are coming from your environment and helps to distinguish between false positives and legitimate threats.
☑️ Identifies new places where protections are required and takes proactive action to ensure any cybersecurity gaps are filled.
☑️ Provides contextual insights that further ensure all your digital assets are secure.
Our Alarm Guardian offer page provides further information on the three tiers of protection available for your organization, and be sure to book a call to discuss your organization’s unique requirements.