As we mark Cybersecurity Awareness Month, it’s essential to consider how the swift pace of technological advancement demands stronger cybersecurity measures to combat increasingly sophisticated threats.
With cybersecurity trends shaping the digital landscape, the impact of emerging technologies on cybersecurity is profound. These technologies not only enhance security measures but also introduce new vulnerabilities that could be exploited by cybercriminals.
The dynamic nature of the field and the constant evolution of threats and protective measures make adopting a proactive standpoint, rather than a reactive one, imperative. The surge in cybersecurity threats undermines the integrity of data, systems, and networks, highlighting the importance of vigilance for both organizations and individuals.
In this blog, we will explore the current state of cybersecurity, examine key trends anticipated for 2025, and offer practical tips to help you prepare as the new year approaches.
Jump to a section:
🌐 The Current Landscape of Cybersecurity and Cyber Threats
🚀 5 Emerging Cybersecurity Trends and Threats in 2025
🔑 Key Cybersecurity Tips to Stay Prepared for 2025 and Mitigate Insider Threats
The Current Landscape of Cybersecurity and Cyber Threats
Cybersecurity threats have been on the rise in recent years, with data breaches and cyberattacks making headlines frequently. The increasing challenges posed by the evolving digital landscape necessitate stronger defenses against cyber security threats.
According to ISACA’s State of Cybersecurity report, 38% of cybersecurity professionals are witnessing a rise in cyber-attacks, an increase from 31% last year. Notably, the primary attack methods are social engineering at 19% and malware at 13%.
Microsoft’s Digital Defense Report 2024 offers further insight. It states that ransomware remains a critical cybersecurity concern, having observed a 2.75x year-over-year increase in human-operated ransomware-linked encounters, where at least one device in a network was targeted.
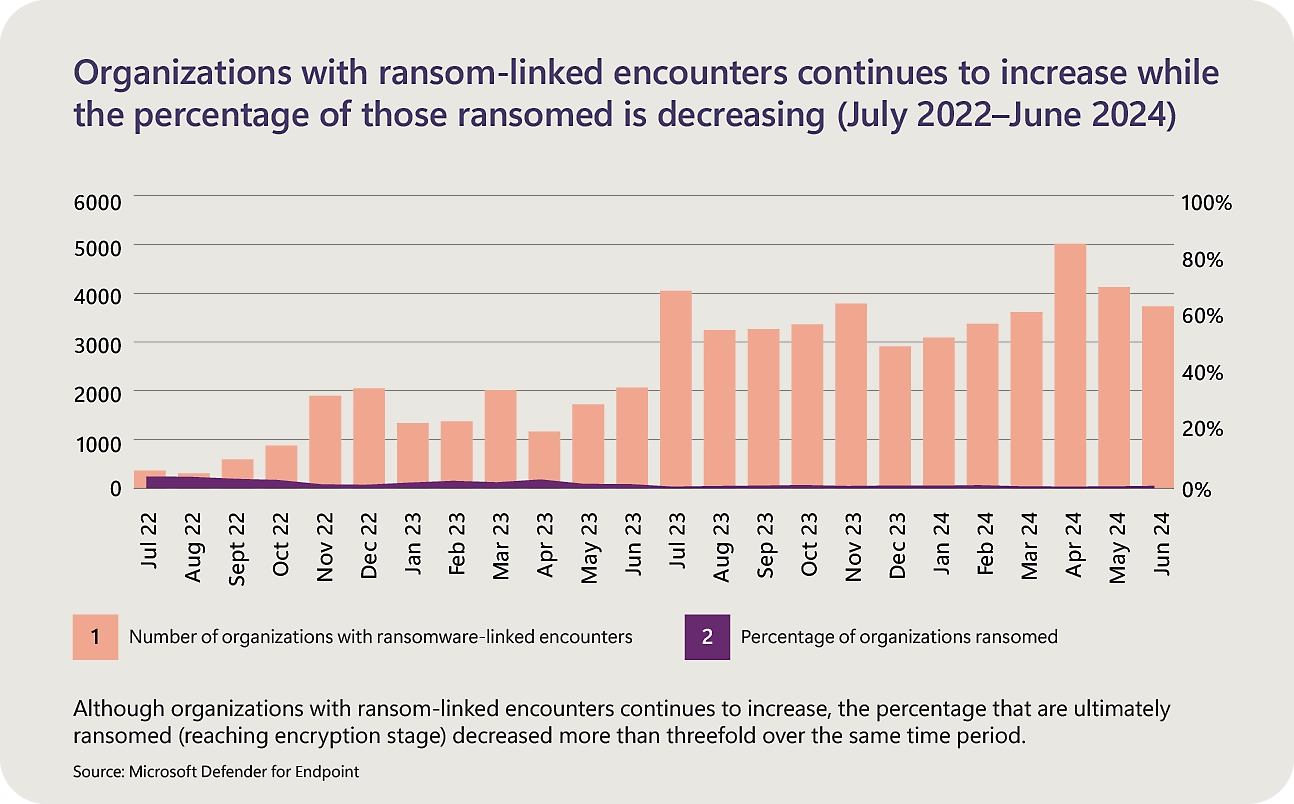
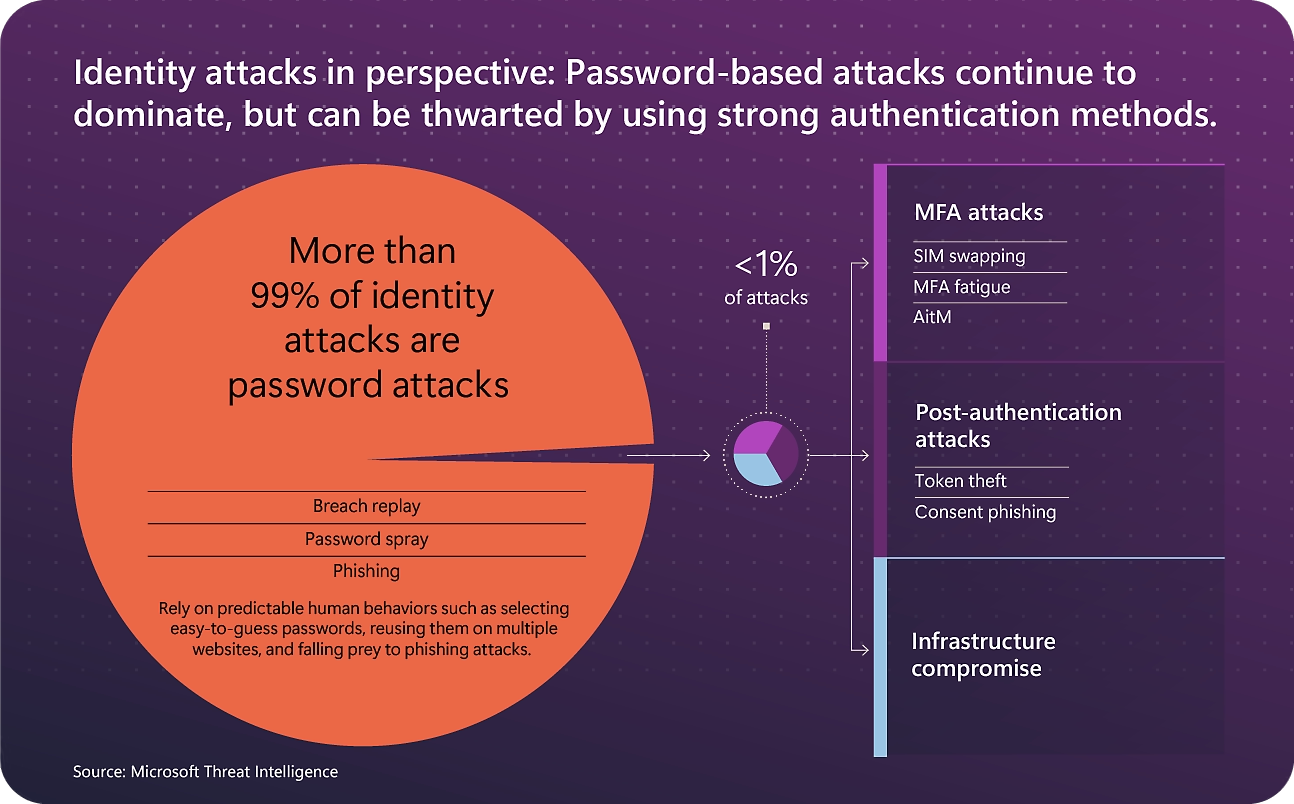
With the shift of organizations to the cloud, identity-related attacks have surged, as adversaries exploit compromised credentials to access vital resources. Per Microsoft’s report, password-based attacks account for over 99% of the 600 million daily identity breaches.
Insider threats also pose significant risks in modern cybersecurity challenges, leading to data breaches and emphasizing the need for enhanced awareness and training to protect sensitive data.
The increasing reliance on technology due to remote work arrangements has also created more vulnerabilities for cybercriminals to exploit. With more devices connected to networks and the proliferation of cloud-based applications and services, the attack surface continues to expand. 47% of companies expect a cyberattack on their organization in the next year.
As individuals and companies prepared for the challenges ahead, global economies prioritized strengthening their cybersecurity policies. In 2024, major economies like the European Union, the United States, and Singapore implemented new laws to enhance these measures.
The World Economic Forum’s Global Cybersecurity Outlook 2024 emphasizes the importance for businesses, organizations, and cyber leaders to consistently invest in and remain aware of crucial security fundamentals. Notably, 60% of executives now agree that cyber and privacy regulations effectively mitigate risks within their organizational ecosystem—reflecting a 21% increase since 2022.
As cyberattacks continue to grow in frequency and complexity, so too does the technology developed to counteract these threats. It is imperative for organizations to not only adopt these advanced technological solutions but also to stay informed about the latest cybersecurity trends and developments.
👉 You may be interested in our blogs on:
👉 Ransomware
👉 Phishing scams
👉 Social Engineering
5 Emerging Cybersecurity Trends and Threats in 2025
1. Cybersecurity and AI
Artificial Intelligence (AI) has been rapidly integrated into various industries, and the cybersecurity world is no exception. AI-powered solutions, including automated security systems, can analyze vast quantities of data quickly, allowing for more efficient threat detection and response. It also enables automated security processes, freeing up time for cybersecurity professionals to focus on other critical tasks.
However, while AI strengthens security postures for organizations, attackers have been increasingly using it to launch sophisticated attacks, and this is going to continue well into 2025. For instance, AI can mimic writing styles and generate realistic emails, making phishing attempts more convincing. This includes the use of AI to translate deceptive emails, allowing attackers to effortlessly expand their operations worldwide.
This has led to the emergence of terms like ‘Dark AI,’ referring to the misuse of artificial intelligence for malicious purposes. Beyond the previously mentioned scenario, AI’s capacity to automatically generate malware variations presents a significant challenge for antivirus solutions. Moreover, AI is refining attacks by accurately identifying data targets and calculating ransom amounts that victims are more likely to pay.
Interestingly enough, Dark AI is likely going to be best countered by AI itself. In 2025, AI-assisted cybersecurity will see significant advancements, with proactive AI predicting and preventing future threats by analyzing patterns and past attacks to foresee potential vulnerabilities.
Organizations will increasingly use AI-driven governance frameworks to automate compliance checks and monitor cybersecurity policies in real-time. This approach addresses the complexity of managing cyber compliance in a digital world. AI systems will continuously audit security practices, ensuring regulatory compliance and mitigating legal and financial risks. Additionally, AI will enable adaptive governance strategies, updating policies based on emerging threats and technological changes, ensuring robust and compliant cybersecurity.
AI and blockchain will continue to play crucial roles in enhancing cybersecurity by automating security systems, detecting threats, preventing data tampering, and providing secure identity management.
This dual-use nature of AI in cybersecurity highlights the urgent need for the development of ethical guidelines and regulations to ensure its responsible application as we head towards 2025.
👉 Read our blog on using artificial intelligence in cybersecurity
2. Post-quantum Cryptography
In addition to AI, quantum computing has also been making significant strides in recent years. Quantum computers' capabilities can potentially break even the most advanced encryption methods used today.
In 2024, Google claimed it achieved 'quantum supremacy,' demonstrating that its quantum computer could solve a problem in a few moments compared to the world's fastest supercomputer that would take 47 years. This breakthrough raises concerns about the safety and security of data encrypted with traditional cryptographic algorithms.
Gartner reports that criminals are already preparing for this shift by employing strategies such as "harvest now, decrypt later." This approach involves exfiltrating encrypted data with the expectation that quantum technology will eventually enable them to decrypt it.
To address this issue, industry experts are looking towards post-quantum cryptography as a solution. These are cryptographic algorithms that are resistant to quantum computing attacks, ensuring data confidentiality and integrity even in the face of advancements in quantum technology.
In 2025, we can expect post-quantum cryptography to become more widely adopted by organizations and governments alike. This will involve replacing current encryption methods with new post-quantum alternatives that can withstand potential quantum attacks.
3. Zero-trust Architecture
Traditional security models often rely on a perimeter-based approach, where trust is placed in users and devices inside the network. However, this has become increasingly inadequate as organizations embrace remote work, cloud computing, and the Internet of Things (IoT). In 2025, we can expect to see an increased focus on zero-trust architecture as a more secure alternative, enhancing security infrastructure within organizations.
Insider threats are a significant risk in modern cybersecurity, often leading to data breaches. Zero-trust architecture helps mitigate these risks by adopting strict access controls and continuous monitoring to protect against internal vulnerabilities.
Zero-trust architecture operates under the principle of “never trust, always verify,” assuming that no user or device within or outside the network can be trusted by default. It continually verifies identity and access permissions before allowing any communication or data transfer. This approach eliminates reliance on traditional firewalls and VPNs, reducing potential attack surfaces.
4. Disinformation Security
In the age of social media and online news, disinformation has become a significant concern. With advances in technology, it's becoming increasingly challenging to distinguish between real and fake information, making it easier for malicious actors to spread false content.
In 2025, we can expect to see the rise of disinformation security as a crucial aspect of cybersecurity. This includes using AI-powered tools to identify and flag potential disinformation campaigns and implementing stricter content moderation policies on social media platforms.
For organizations, one of the most salient use cases would be to prevent the impersonation of any of their employees, leadership or any other stakeholders in their sphere.
Gartner's Dan Ayoub explains it best. He says, "Suppose an employee receives an email that appears to be from your company’s CEO, requesting sensitive information or authorizing a financial transaction. Disinformation security tools would analyze the email’s content, metadata and origin to detect signs of impersonation or fraud, and if need be, automatically quarantine the email, alert the employee and notify IT security."
5. Cloud Security Mesh and Cloud Security Measures
As cloud adoption accelerates, organizations are diversifying their cloud services portfolios, often utilizing a mix of public, private, and hybrid clouds. This shift presents unique security challenges, as traditional network perimeter defenses are ill-suited to protect the broader, more distributed cloud infrastructure.
Implementing robust cloud security measures is crucial to address the unique challenges posed by cloud computing, such as data breaches and cyber threats. Essential strategies include encryption and authentication, which are necessary as more organizations adopt cloud-first approaches and navigate complex regulatory environments.
By 2025, cloud security mesh frameworks will become essential in addressing these challenges, offering a flexible and modular approach to securing diverse assets, regardless of location. This architecture facilitates the integration of disparate security services and policy enforcement across multiple environments, enabling organizations to apply consistent security controls and maintain visibility into their cloud-based operations.
Coupling this with AI-driven insights can enhance threat detection and response, ensuring that even as cloud environments grow in complexity, they remain secure and resilient against emerging threats.
Key Cybersecurity Tips to Stay Prepared for 2025 and Mitigate Insider Threats
🔧 Regularly Update and Patch Systems: Ensure that all software applications and systems are consistently updated to the latest versions. Regular patches and updates close vulnerabilities that can be exploited by cybercriminals and are crucial for maintaining robust security defenses.
👩🏫 Conduct Continuous Security Training: Regularly train employees and leadership on cybersecurity best practices and the latest threats. By fostering a culture of security awareness, organizations can reduce the likelihood of human error leading to breaches and ensure that all staff members remain vigilant. The integration of personal devices into work tasks leads to blurred boundaries between personal and professional life, increasing vulnerability to cyber threats.
🔒 Implement Multi-Factor Authentication (MFA): Strengthen access control by deploying MFA for all sensitive systems and data access points. MFA provides an additional layer of security beyond passwords, significantly reducing the risk of unauthorized access.
🔎 Perform Regular Security Audits: Conduct comprehensive and periodic security audits to identify vulnerabilities and assess the effectiveness of current security measures. Audits help in pinpointing areas for improvement and ensuring compliance with regulatory requirements.
📍 Develop and Test Incident Response Plans: Create a well-defined incident response plan to quickly and efficiently handle any security breaches or cyber incidents. Conduct regular simulations and drills to ensure that all team members are familiar with their roles and responsibilities during a cybersecurity event.
Are you confident in your cybersecurity defenses?
Understanding your threat landscape is essential to staying protected. We provide a complimentary Cybersecurity Risk Assessment Report to give you clear insights, including login activity analysis and dark web exposure, so you can act before threats escalate.
If staying secure is a priority, let's start today!
👉 Read our blog on four strategies to safeguard your digital assets
Conclusion
As we move toward 2025, the cyber landscape is set to evolve in unprecedented ways. From the challenges of AI-driven threats to the implications of quantum computing, staying ahead of cybersecurity trends isn’t just advisable; it's essential for individuals and organizations alike. By adopting proactive measures, regularly updating security frameworks, and keeping abreast of new technologies, we can all play a part in building a safer digital future. Every step you take to strengthen your cybersecurity today will pay dividends as you face tomorrow's challenges.
Take charge of your cybersecurity journey today!
Start with ProServeIT's 3-Step Security Foundation to protect your organization from evolving threats. From email and identity security to robust data protection, our solutions are tailored to keep you safe. These include:
✔️ Email Security
✔️ Identity Security
✔️ Data Security
Don’t wait until it’s too late—reach out now for a complimentary Threat Landscape Assessment and gain critical insights to secure your digital environment. Protect what matters, and step confidently into the future.
In recognition of Cybersecurity Awareness Month, remember: Trust no one, always verify. Stay secure!

October 31, 2024





Comments